Right now, people around the world are taking to the streets to protest against issues like police brutality and systemic racism. It's a fundamental right to make your voice heard, but governments often have ways to watch and track protesters. We've seen examples of this, like when the U.S. Justice Department tried to get IP addresses of over a million people who organized protests online. This shows how easy it can be for authorities to gather information, especially in the digital age.
This guide isn't about telling you whether or not to protest. It's about helping you do it safely, so you can exercise your rights without putting your privacy at risk. This is particularly important because in many places, the freedom to protest is under threat.
Understanding the Risks
Before diving into solutions, let's understand the ways your privacy can be compromised during a protest:
- Digital Tracking: Your smartphone is a goldmine of personal data. Location tracking, app usage, and even your social media activity can be monitored.
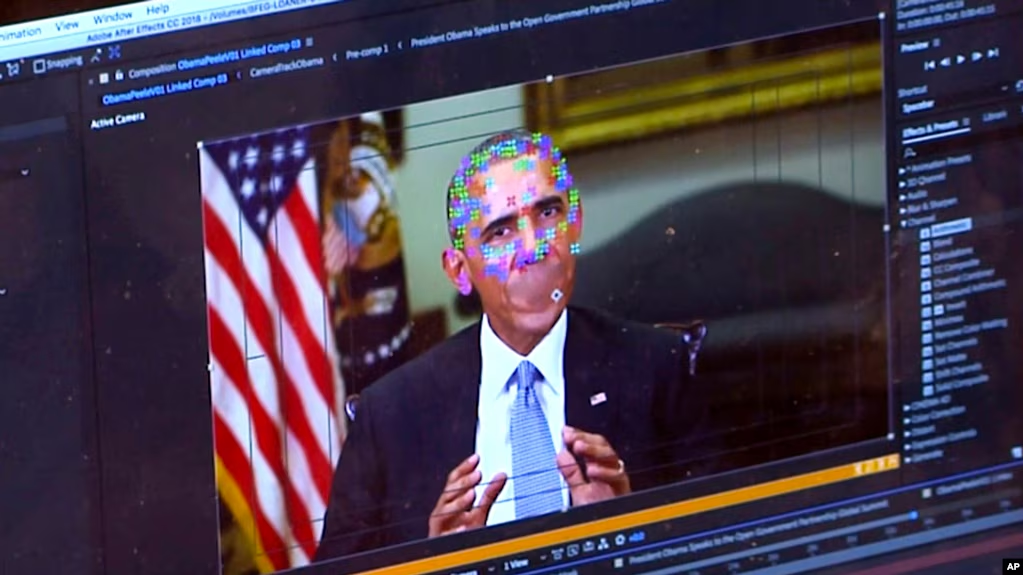
- Facial Recognition: Cameras in public spaces, and even those used by law enforcement, can identify you using facial recognition technology.
- Phone Confiscation: If your phone is seized, authorities can access all your data, including messages, photos, and contacts.
- Social Media Monitoring: Police and other agencies can monitor social media posts, hashtags, and groups to identify and track protesters.
- Data Collection from Organizers: As seen with the IP address example, organizers' platforms can be targeted for data collection.
- Physical Surveillance: Plainclothes officers or other forms of physical surveillance can be used to gather information about protesters.
Practical Steps to Protect Your Privacy
Here's how you can minimize the risks and protect your identity while protesting:
Before the Protest
- Use a Burner Phone: If possible, use a cheap, prepaid phone that isn't linked to your personal information. Only use it for protest-related communication.
- Secure Your Main Phone: If you must use your main phone, turn off location services, Bluetooth, and Wi-Fi. Use a strong passcode.
- Encrypt Your Phone: Enable full disk encryption on your phone to protect your data in case it's confiscated.
- Clean Up Your Social Media: Remove or hide any posts that could identify you or reveal your protest plans. Consider using a temporary, anonymous social media account.
- Use a VPN: A Virtual Private Network (VPN) encrypts your internet traffic and masks your IP address, making it harder to track your online activity. Choose a reputable VPN provider.
- Use Secure Messaging Apps: Use encrypted messaging apps like Signal or Telegram for communication with other protesters. These apps offer end-to-end encryption, meaning only you and the recipient can read the messages.
- Plan Your Route and Communication: Discuss a plan with your group, including meeting points, communication methods, and what to do if you get separated.
- Dress Appropriately: Wear clothing that doesn't easily identify you. Avoid wearing anything with your name or personal information. Cover tattoos or other unique identifiers.
- Prepare a Protest Kit: Include essentials like water, snacks, first-aid supplies, and a power bank for your phone.
- Know Your Rights: Familiarize yourself with your rights as a protester, including your right to record police activity and your right to remain silent if questioned.
During the Protest
- Minimize Phone Usage: Only use your phone when absolutely necessary. Keep it in airplane mode when possible.
- Be Aware of Your Surroundings: Watch for cameras and other surveillance equipment. Be cautious about sharing personal information with strangers.
- Avoid Using Public Wi-Fi: Public Wi-Fi networks are often unsecured and can be easily monitored.
- Document Everything: If you witness any police misconduct or violations of your rights, document it with photos or videos. However, be mindful of your surroundings and prioritize your safety.
- Stay in a Group: Stick with your group and avoid being alone. There's safety in numbers.
- Communicate with Your Group: Use your secure messaging app to stay in touch with your group and share updates.
- Be Mindful of Facial Recognition: Wear a mask, sunglasses, or a hat to make it harder for facial recognition software to identify you.
- Don't Engage with Provocateurs: Be aware of individuals who may be trying to incite violence or disrupt the protest.
- Know Your Exit Strategy: Plan an escape route in case the protest turns violent or you need to leave quickly.
After the Protest
- Clean Up Your Digital Footprint: Delete any photos or videos you took that could identify you or other protesters. Clear your browsing history and cache.
- Secure Your Devices: Change your passwords and update your software. Scan your devices for malware.
- Monitor Your Accounts: Keep an eye on your bank accounts and credit reports for any suspicious activity.
- Debrief with Your Group: Discuss what happened during the protest and share any concerns or observations.
- Support Other Protesters: Share information and resources with other protesters to help them protect their privacy.
- Document Your Experiences: Write down your experiences, including any interactions with law enforcement. This can be helpful if you need to file a complaint or take legal action.
- Stay Informed: Keep up-to-date on the latest privacy and security threats.
Beyond the Basics: Deeper Insights
The Importance of Digital Literacy: Understanding how technology works is crucial for protecting your privacy. Learn about encryption, VPNs, and other security tools. Educate yourself and others about the risks of digital surveillance.
Building Community Resilience: Protecting your privacy is not just an individual responsibility. It's a collective effort. Build strong relationships with other protesters and create a network of support. Share information and resources, and look out for each other.
Legal Considerations: Be aware of the laws in your area regarding protests and surveillance. Consult with a lawyer if you have any questions or concerns. Know your rights and be prepared to assert them.
The Role of Technology Companies: Hold technology companies accountable for their role in enabling surveillance. Demand transparency and accountability from companies that collect and share your data.
Long-Term Strategies: Protecting your privacy is an ongoing process. Develop long-term strategies for protecting your data and staying safe online. This includes regularly updating your software, using strong passwords, and being cautious about sharing personal information.
Understanding Surveillance Tactics: Become familiar with the different types of surveillance used by governments and law enforcement. This includes facial recognition, location tracking, and social media monitoring. Knowing how these technologies work can help you take steps to protect yourself.
The Psychological Impact: Constant surveillance can have a negative impact on mental health. Be aware of the psychological effects of surveillance and take steps to protect your well-being. This includes limiting your exposure to news and social media, and seeking support from friends, family, or a therapist.
The Future of Protests: As technology continues to evolve, so will the tactics used to monitor and track protesters. Stay informed about the latest developments and adapt your strategies accordingly. Consider using decentralized platforms and technologies that prioritize privacy.
By taking these steps, you can help protect your privacy and exercise your right to protest safely and effectively. Remember, your safety and privacy are paramount. Stay vigilant, stay informed, and stay safe.
Keeping Your Smartphone Private During Protests and Beyond
In today's world, our smartphones hold a vast amount of personal information, making them a potential liability during protests or any situation where privacy is a concern. While the ideal solution might be to leave your phone at home, that's often impractical. We rely on these devices for communication, navigation, and even documenting important events. So, how can you protect your privacy while still using your smartphone? Let's explore some practical steps.
The Ideal: No Phone at All
The most secure option is, of course, to avoid taking your primary phone. However, this is seldom realistic. Phones are essential for emergencies, coordinating with others, and, as we've seen, documenting crucial events. The ability to capture and share footage of protests has played a vital role in raising awareness and driving change.
The Next Best Thing: A Dedicated "Protest Phone"
If possible, consider using a separate, inexpensive phone specifically for protests or situations where privacy is a concern. This "protest phone" should contain only essential apps and minimal personal data.
- Limited Apps: Install only the apps you absolutely need, such as secure messaging apps, a camera app, and a map application. Avoid social media, banking, or any app that stores sensitive information.
- No Personal Accounts: Don't log in to your personal email, social media, or other accounts on this device.
- Wipe Before and After: Before and after each use, consider wiping the phone to ensure no data remains.
This approach minimizes the risk of your personal data being exposed if the phone is confiscated. However, we understand that acquiring a second phone isn't always feasible.
Securing Your Primary Phone
If using a dedicated phone isn't an option, you can take steps to secure your primary device:
- Temporary App Removal: Delete non-essential apps before attending a protest. Reinstall them afterward.
- Log Out: Log out of all apps and accounts, including social media, email, and banking.
- Disable Location Services: Turn off GPS, Wi-Fi, and Bluetooth to prevent tracking. You can usually find these settings in your phone's control center or settings menu.
- Airplane Mode: For maximum isolation, enable airplane mode. However, this will limit your ability to communicate.
- Consider a Burner SIM: If possible, use a prepaid SIM card that isn't linked to your personal information.
Private Messaging Apps: Secure Communication
Communication is vital during protests. Choose messaging apps that prioritize privacy and security. Look for apps with:
- End-to-End Encryption: This ensures that only the sender and recipient can read messages. Popular options include Signal.
- Open-Source Code: Open-source apps allow security experts to verify their code, ensuring transparency.
- Minimal Data Collection: Choose apps that collect as little user data as possible.
- Disappearing Messages: Some apps offer the option to automatically delete messages after a set period.
Avoid using standard SMS or messaging apps that don't offer end-to-end encryption.
Faraday Bags: Blocking Signals
A Faraday bag is a simple yet effective way to block all signals to and from your phone. These bags are made of conductive materials that create an electromagnetic shield.
- Complete Signal Blockage: When your phone is inside a Faraday bag, it cannot send or receive calls, texts, or data.
- Location Privacy: This prevents your location from being tracked via GPS or cellular towers.
- Considerations: Remember that you will be completely unreachable while your phone is in the bag. You will need to remove it to use it.
Encryption: Protecting Your Data
If your phone is confiscated, encryption is your last line of defense.
- Full Disk Encryption: Enable full disk encryption on your Android device (Settings -> Security -> Encrypt Disk). iPhones have this enabled by default when you set a passcode.
- Strong Passwords: Use a long, complex password or passphrase that is difficult to guess. Avoid using easily guessable patterns or personal information.
- Avoid Biometrics: Fingerprint and facial recognition can be easily bypassed. Use a strong password instead.
- App-Specific Passwords: Many apps, especially secure messaging apps, allow you to set separate passwords. Use this feature to add an extra layer of protection.
It is important to understand that if the device is turned on, and the device is forced to unlock, then there is a potential for data extraction. If the device is off, and fully encrypted, then data extraction becomes much more difficult.
VPNs: Hiding Your IP Address
Your IP address can reveal your location and browsing activity. A Virtual Private Network (VPN) can help mask your IP address and encrypt your internet traffic.
- IP Masking: A VPN routes your internet traffic through a remote server, making it appear as if you are browsing from that server's location.
- Encryption: VPNs encrypt your internet traffic, protecting it from eavesdropping.
- Choosing a VPN: Select a reputable VPN provider that has a strict no-logs policy and uses strong encryption protocols.
- Considerations: Free VPNs may log your data or sell it to third parties. Paid VPNs offer better security and privacy.
- Always On: Configure your VPN to automatically connect when you turn on your device.
Remember, while a VPN can enhance your privacy, it's not foolproof. It's crucial to choose a trustworthy provider.
Practical Advice and Additional Insights
- Regular Software Updates: Keep your phone's operating system and apps up to date to patch security vulnerabilities.
- Be Aware of Your Surroundings: Pay attention to who is around you and avoid sharing sensitive information in public places.
- Document Everything: If you are documenting a protest, consider using a separate camera or recording device.
- Data Backups: Regularly back up your important data to a secure location. If your phone is confiscated, you will still have access to your files.
- Practice OpSec(Operational Security): Consider what information you share online, and with whom. Be cautious about the metadata that your devices create.
- Understand Legal Implications: Research the laws in your area regarding protests and privacy.
- Educate Others: Share this information with friends and family to help them protect their privacy.
- Physical Security: Consider a durable phone case and screen protector to prevent physical damage.
By taking these precautions, you can significantly reduce the risk of your personal data being exposed during protests or any situation where privacy is a concern. Remember, privacy is an ongoing process, and it's essential to stay informed about the latest security threats and best practices.
Social Media: A Double-Edged Sword in the Digital Age
Social media has revolutionized how we connect, share information, and organize. But in today's world, it's crucial to understand that your online presence can be a powerful tool, and unfortunately, a potential vulnerability, especially when participating in protests or any activity that might attract unwanted attention. Think of it like this: every post, every like, every shared image is a breadcrumb, leaving a trail that can lead directly to you.
Your Digital Footprint: More Than Just Likes and Shares
Your social media profile is a digital mirror, reflecting your identity, interests, and connections. Consider this: a simple Facebook post announcing a protest can inadvertently reveal your location, your network of friends, and even your political leanings. This information, when combined with other online data, can create a comprehensive picture of you. If you're logged into your social media accounts on your phone, you're essentially carrying a tracking device that pinpoints your location and connects it to your personal identity.
Practical Advice:
- Log Out: Before participating in any event where your privacy might be compromised, log out of all social media accounts on your phone. Don't just close the app; actively log out.
- Temporary Deletion: For heightened security, consider temporarily deleting social media apps from your phone. You can reinstall them later.
- Separate Devices: If possible, use a burner phone or a device that isn't linked to your primary accounts for communication during sensitive events.
- VPN Usage: Use a reputable Virtual Private Network (VPN) to mask your IP address and encrypt your internet traffic. This makes it harder to track your online activity.
- Disable Location Services: Turn off location services on your phone to prevent apps from tracking your whereabouts.
The Perils of Sharing Protest Content
Sharing images and videos from protests can be a powerful way to raise awareness. However, it's essential to prioritize the privacy and safety of others. Unblurred faces and identifiable features can lead to individuals being targeted by authorities or other groups. Remember, what you share online can have real-world consequences.
Practical Advice:
- Blur Faces: Before sharing any images or videos, use editing tools to blur the faces of all individuals present.
- Obscure Identifiable Features: Pay attention to other identifiable features, such as tattoos, clothing, or unique surroundings.
- Consider the Content: Think carefully about the content you share. Avoid posting anything that could be used to incriminate yourself or others.
- Metadata Removal: Remove metadata from images and videos before sharing. Metadata can contain information about the location, time, and device used to capture the content.
- Timing: Avoid posting in real time. Delay posting by several hours or even days to make it harder to correlate your posts with your physical location.
- Verify Information: Before sharing any information, verify its accuracy. Spreading misinformation can have serious consequences.
The Long-Term Implications of Your Digital Presence
Social media platforms like Facebook and WhatsApp collect vast amounts of data about their users. This data can include your location history, messaging logs, and even your browsing habits. While deleting your account can remove your public profile, it's important to understand that some data may still be retained by the platform.
Practical Advice:
- Review Privacy Settings: Regularly review and adjust your privacy settings on all social media accounts. Limit the amount of information you share publicly.
- Use Secure Messaging Apps: Consider using encrypted messaging apps like Signal or Telegram, which offer enhanced privacy and security features.
- Limit App Permissions: Review the permissions granted to apps on your phone. Limit access to sensitive information, such as your contacts, location, and camera.
- Data Minimization: Practice data minimization by sharing only the information that is absolutely necessary.
- Two-Factor Authentication: Enable two-factor authentication on all your accounts to add an extra layer of security.
- Password Management: Use strong, unique passwords for each of your accounts and consider using a password manager.
Beyond Social Media: A Holistic Approach to Digital Security
Protecting your digital privacy requires a holistic approach that goes beyond social media. Here are some additional considerations:
- Secure Your Devices: Use strong passwords or biometric authentication to secure your devices. Keep your software and apps up to date to patch security vulnerabilities.
- Be Aware of Phishing: Be cautious of phishing emails and messages that attempt to trick you into revealing personal information.
- Limit Public Wi-Fi Usage: Avoid accessing sensitive information on public Wi-Fi networks, which are often unsecured.
- Educate Yourself: Stay informed about the latest digital security threats and best practices.
- Consider the Cloud: Be mindful of the information you store in the cloud. Cloud services can be vulnerable to data breaches.
- Digital Detox: Periodically disconnect from technology to reduce your digital footprint and improve your mental well-being.
The Importance of Community and Collective Security
Protecting your digital privacy is not just an individual responsibility; it's also a collective effort. Share your knowledge and best practices with your friends, family, and community. By working together, we can create a safer and more secure digital environment for everyone.
In conclusion, social media is a powerful tool that can be used for both good and bad. By understanding the potential risks and taking proactive steps to protect your privacy, you can navigate the digital landscape with greater confidence and security. Remember that every digital action leaves a trace, and thoughtful consideration is key to protecting yourself and others in the digital age.
Staying Safe From Surveillance: A Practical Guide
In today's world, it's not just your phone or social media that can reveal your location or identity. Authorities and even private entities have access to a wide range of surveillance tools, from CCTV cameras to sophisticated facial recognition software. Understanding these techniques and taking proactive steps to protect yourself is crucial for maintaining your privacy and safety.
Beyond Your Phone: Understanding the Scope of Surveillance
We often focus on digital footprints, but physical surveillance is equally important. Think about the sheer number of security cameras in public spaces, shopping malls, and even residential areas. These cameras, combined with advanced software, can track your movements and identify you with alarming accuracy. Police departments and other agencies regularly use this technology for investigations and monitoring. Even private companies use it for marketing and security purposes.
Here's a breakdown of common surveillance methods:
- CCTV and Video Surveillance: Cameras are everywhere, and many are now equipped with AI-powered features like facial recognition and object tracking.
- Facial Recognition: This technology can identify individuals from images or videos, even with partial facial coverings.
- License Plate Readers: These systems automatically capture and record license plate numbers, tracking vehicle movements.
- Location Tracking: Beyond your phone, other devices like smartwatches and even some vehicles can transmit location data.
- Biometric Data Collection: This includes fingerprinting, iris scanning, and even gait analysis, which can uniquely identify individuals.
Practical Steps to Minimize Your Visibility
The goal is to make yourself as difficult to identify as possible. This doesn't mean you need to become invisible, but rather to adopt a few simple strategies.
Clothing and Appearance
Your clothing can significantly impact your visibility. Consider these tips:
- Muted Colors: Opt for neutral colors like gray, black, navy, or brown. These colors blend into the background and make you less noticeable. Avoid bright colors or patterns that draw attention.
- Layered Clothing: Layering allows you to quickly change your appearance by adding or removing items.
- Avoid Identifiable Logos or Brands: Clothing with prominent logos or brand names can make you easily recognizable.
- Conceal Identifiable Features: If you have distinctive features like tattoos, piercings, or birthmarks, consider covering them with clothing or makeup.
- Hats and Scarves: These can help obscure your face and hair, making it harder to identify you.
Face and Head
Your face is your most recognizable feature. Here's how to protect it:
- Face Masks: As mentioned, face masks provide a double layer of protection. They obscure your facial features and protect against airborne illnesses. Choose masks that cover a significant portion of your face.
- Sunglasses: Sunglasses hide your eyes, which are a key component of facial recognition. Opt for larger sunglasses that provide maximum coverage.
- Hats or Hoodies: These can further obscure your face and hair, especially when combined with a mask and sunglasses.
- Consider a Change in Hairstyle: A simple change in hairstyle, like wearing a wig or changing your part, can significantly alter your appearance.
- Avoid Distinctive Makeup: If you wear makeup, avoid bold or distinctive styles that make you easily recognizable.
Behavior and Movement
Your behavior and movement patterns can also reveal your identity. Consider these points:
- Vary Your Routes: Avoid taking the same route every day. This makes it harder to track your movements.
- Be Aware of Your Surroundings: Pay attention to security cameras and other surveillance devices.
- Avoid Lingering in One Place: Moving around frequently makes it harder to track you.
- Change Your Gait: Altering your walking style can make you less recognizable to gait analysis software.
- Minimize Digital Footprints in Public: Avoid connecting to public Wi-Fi networks without a VPN, and disable location services on your devices when not needed.
Protecting Your Online Identity
Beyond physical surveillance, your online presence can also be a source of vulnerability. Opponents or malicious actors may resort to doxxing, which involves revealing your personal information online, or engaging in online harassment to silence you. Here's how to mitigate these risks:
Reducing Your Online Footprint
- Review Your Social Media Profiles: Remove or limit personal information, such as your address, phone number, and date of birth. Adjust privacy settings to restrict access to your posts and photos.
- Use a Pseudonym: Consider using a pseudonym or nickname online, especially on platforms where you discuss sensitive topics.
- Limit Sharing Personal Information: Be cautious about sharing personal information online, even in private messages.
- Use a VPN: A Virtual Private Network (VPN) encrypts your internet traffic and masks your IP address, making it harder to track your online activity.
- Use Secure Messaging Apps: Opt for messaging apps that offer end-to-end encryption, such as Signal or WhatsApp.
- Use Strong Passwords and Two-Factor Authentication: Protect your online accounts with strong, unique passwords and enable two-factor authentication whenever possible.
- Regularly Search for Your Information Online: Use search engines to find information about yourself and request the removal of any unwanted or inaccurate content.
- Use Privacy-Focused Search Engines: Consider using search engines like DuckDuckGo or Startpage, which prioritize user privacy.
Dealing with Doxxing and Online Harassment
- Document Everything: If you are targeted by doxxing or online harassment, document everything, including screenshots, emails, and messages.
- Report the Abuse: Report the abuse to the platform where it occurred and to law enforcement if necessary.
- Seek Support: Reach out to friends, family, or support groups for emotional support.
- Consider Legal Action: If the harassment is severe or poses a threat to your safety, consider consulting with an attorney.
Staying Vigilant: A Continuous Effort
Protecting yourself from surveillance is an ongoing process. Technology is constantly evolving, and new surveillance methods are being developed all the time. Staying informed and adapting your strategies is crucial.
Remember that no single measure can guarantee complete protection. The most effective approach is to combine multiple strategies and stay vigilant both online and offline.
Here are some additional points to consider:
- Be Aware of Your Digital Devices: Your smartphone, laptop, and other devices can be tracked and monitored. Regularly update your software and use strong passwords.
- Protect Your Home Network: Secure your home Wi-Fi network with a strong password and consider using a VPN.
- Be Cautious About Sharing Location Data: Disable location services on your devices when not needed and be mindful of apps that request location access.
- Educate Yourself: Stay informed about the latest surveillance technologies and privacy best practices.
- Support Privacy-Focused Initiatives: Support organizations and initiatives that advocate for privacy rights.
By taking these steps, you can significantly reduce your risk of being tracked or identified, protecting your privacy and safety in an increasingly surveilled world.




























0 Comments