The Tor Browser is a powerful tool designed to give you privacy and freedom online. It lets you browse the internet anonymously, making it harder for anyone to track your activity. Think of it as a digital cloak, hiding your tracks as you explore the web.
However, like any powerful tool, it needs to be used with care. While Tor opens up a world of possibilities, including access to the Dark Web, it also comes with potential risks. It's crucial to understand these risks and take steps to protect yourself.
Understanding Tor's Core Function
Tor works by routing your internet traffic through a network of volunteer-operated servers, called "nodes." Each node encrypts your data, so by the time it reaches its destination, it's been through multiple layers of encryption. This makes it incredibly difficult to trace the traffic back to you. This is why it is used by journalists, activists, and people in countries with heavy censorship.
Imagine sending a letter through a series of post offices, each one sealing it in a new envelope. By the time it reaches the recipient, no one along the way knows who sent it. That's essentially how Tor works.
Why Use Tor?
- Privacy: Tor hides your IP address and browsing history, preventing websites and ISPs from tracking you.
- Anonymity: It allows you to browse the web without revealing your identity.
- Access to Restricted Content: Tor can bypass censorship and access websites that are blocked in your region.
- Protecting Sensitive Information: For whistleblowers, journalists, and activists, Tor offers a secure way to communicate and share information.
The Dark Web: A Double-Edged Sword
The Dark Web, accessible through Tor, is a part of the internet not indexed by regular search engines. It's known for its anonymity, but it's also home to illegal activities and potentially harmful content. It's like exploring a hidden city: there are interesting things to discover, but also dangerous areas to avoid.
Think of the Dark Web as a collection of hidden services, which are websites that are only accessible through the Tor network. These services often have ".onion" addresses, which are difficult to remember and not searchable through regular search engines.
Essential Safety Measures When Using Tor
Here's how to stay safe while using Tor:
-
Configure Tor's Security Settings:
Tor offers different security levels. Higher security levels disable features like JavaScript, which can be used to track you. To adjust these settings, click the "Onion" icon in the Tor Browser toolbar and select "Security Settings."
Consider setting the security level to "Safest" when visiting sensitive websites or exploring the Dark Web. This will disable JavaScript and certain other features, providing maximum protection.
Remember, disabling JavaScript can break some websites, so you may need to adjust the settings depending on your browsing needs.
-
Avoid Unverified Websites and Suspicious Links:
This is crucial, especially on the Dark Web. Many websites are designed to steal your information or infect your computer with malware. Be wary of websites with poor design, strange URLs, or requests for personal information.
Never click on links from untrusted sources, and always double-check the URL before entering any sensitive information. Look for common phishing techniques, such as misspellings or slightly altered domain names.
One practical tip is to use a password manager. This way, you don't enter your passwords manually, reducing the risk of keyloggers stealing your credentials.
-
Use a Secure and Reliable VPN:
A VPN encrypts your internet connection before it enters the Tor network, adding an extra layer of security. This combination, known as "Tor over VPN," makes it even harder for anyone to track your activity.
A VPN hides your real IP address from your ISP and anyone monitoring the first node of the Tor network. This is particularly important if you live in a country with strict surveillance laws.
When choosing a VPN, look for providers with a strict no-logs policy, strong encryption, and a wide range of server locations. Consider reputable VPN providers that have been audited by independent security firms.
For example, using a VPN that has a kill switch, will disconnect your internet if the VPN connection drops, preventing your real IP address from being exposed. Also, split tunneling, will allow you to choose what traffic goes through the VPN, and what traffic doesn't.
-
Keep Tor Browser Updated:
Tor developers release updates regularly to patch security vulnerabilities. Ensure that your Tor Browser is always up to date by enabling automatic updates or manually checking for updates.
-
Don't Download Files Through Tor:
Downloading files through Tor can expose your IP address. The file may be downloaded outside of the Tor network, revealing your true location. If you must download files, use a separate, secure file-sharing service outside of Tor.
-
Disable Plugins:
Plugins like Flash and QuickTime can be exploited to reveal your IP address. Disable them in your browser settings.
-
Use HTTPS Everywhere:
HTTPS encrypts the connection between your browser and the website you're visiting. Use the HTTPS Everywhere extension to ensure that you're always using a secure connection when available.
-
Be Mindful of What You Share:
Even with Tor, avoid sharing personal information that could identify you. This includes your name, address, phone number, and social media profiles. Be cautious about the information you post on forums or social media platforms accessible through Tor.
-
Use Tails OS:
For maximum security, consider using Tails (The Amnesic Incognito Live System), an operating system designed for privacy and anonymity. Tails routes all internet traffic through Tor and leaves no trace on the computer after use.
The Importance of a VPN with Tor
Using a VPN in conjunction with Tor, often referred to as "Tor over VPN," offers an additional layer of protection. Here's why:
- Hides Your Tor Usage from Your ISP: Your ISP can see that you're connecting to the Tor network, but they can't see what you're doing within it. A VPN hides this fact, making it harder for your ISP to monitor your activity.
- Protects Against Malicious Tor Nodes: While rare, some Tor nodes may be compromised. A VPN encrypts your traffic before it enters the Tor network, protecting you from potential attacks.
- Bypasses Tor Blocking: Some networks or countries may block Tor connections. A VPN can bypass these blocks, allowing you to access the Tor network.
- Enhanced Anonymity: Combining a VPN with Tor makes it even harder to trace your activity back to you.
When choosing a VPN for use with Tor, prioritize providers with a strong no-logs policy, robust encryption, and a wide range of server locations.
Remember, while Tor and VPNs provide a high level of anonymity, no system is completely foolproof. Always exercise caution and be mindful of your online activities.
Staying informed about potential threats and practicing safe browsing habits are essential for a secure and private online experience.
Understanding Tor: Your Guide to Anonymous Browsing
Imagine sending a letter, but instead of going directly to the recipient, it passes through several post offices around the world. Each post office opens only one layer of the envelope, revealing only the next destination. This is essentially how Tor, or The Onion Router, works. It's a powerful tool for enhancing your online privacy and anonymity.
What Exactly is Tor?
Tor is an open-source software that allows you to browse the internet anonymously. It's designed to hide your IP address and online activities, making it difficult for anyone to track your movements. While its origins are tied to the U.S. Navy for secure communications, it's now a widely accessible tool for everyone.
How Does Tor Achieve Anonymity?
Tor's magic lies in its network of volunteer-operated servers, known as nodes. When you use the Tor browser, your internet traffic doesn't go directly to the website you're visiting. Instead, it takes a scenic route through multiple nodes, each adding a layer of encryption, much like the layers of an onion. This multi-layered encryption is the core of Tor's anonymity.
The Journey Through the Onion: A Step-by-Step Breakdown
- Initiation and Encryption: When you initiate a connection, your data is wrapped in multiple layers of encryption. Each layer acts as a protective shield, hiding the data's contents and its final destination.
- Entry Node: Your encrypted data first reaches the entry node, the first server in the Tor network. This node decrypts the outermost layer, revealing the next node in the route. However, it doesn't know your original IP address or the final destination.
- Middle Nodes (Relay Nodes): The data then travels through a series of middle nodes. Each node decrypts another layer, revealing the next hop. This process continues, ensuring that no single node knows the complete path of your data.
- Exit Node: Finally, the data reaches the exit node, the last server in the Tor circuit. This node decrypts the final layer of encryption and sends the data to the destination website. At this point, the website sees the exit node's IP address, not your own.
- Return Trip: The website's response follows a similar route back through the Tor network, ensuring end-to-end anonymity.
Key Insights:
- No Single Point of Failure: The distributed nature of the Tor network means there's no central server that can be compromised or monitored.
- Dynamic Routing: Tor circuits are randomly generated and change frequently, making it even harder to track your online activities.
- Encryption at Every Hop: Each node only decrypts one layer of encryption, ensuring that no single entity can see the entire data flow.
Practical Advice for Using Tor
While Tor provides a strong layer of anonymity, it's not foolproof. Here are some practical tips to maximize your privacy:
- Use HTTPS: Always ensure that the websites you visit use HTTPS. This encrypts the communication between your browser and the website, even after your data exits the Tor network.
- Disable Scripts: JavaScript and other scripting languages can reveal your IP address and other identifying information. Consider disabling them or using a script-blocking extension.
- Avoid Logging In: Logging into online accounts while using Tor can compromise your anonymity. If you need to access sensitive accounts, consider using a separate browser or a dedicated operating system.
- Don't Download Torrents: Torrenting over Tor is strongly discouraged. It can expose your IP address and significantly slow down the Tor network for other users.
- Keep Tor Updated: Always use the latest version of the Tor browser to benefit from security patches and improvements.
- Use a VPN with Tor (with caution): While Tor provides anonymity, a VPN can add an extra layer of encryption and hide your Tor usage from your ISP. However, it's crucial to choose a reputable VPN provider that doesn't log your activity, and generally, using a VPN before connecting to Tor is recomended.
- Be Mindful of Plugins and Extensions: Many browser extensions can leak your IP address or other sensitive information. Only install trusted extensions from reputable sources.
- Use Tails or Whonix: For maximum security, consider using Tails (The Amnesic Incognito Live System) or Whonix, operating systems designed specifically for anonymity and privacy.
The Trade-Off: Speed and Performance
One of the most significant drawbacks of using Tor is its speed. Because your data is being routed through multiple servers around the world, there's a noticeable performance hit. Expect slower loading times, especially for websites with heavy multimedia content. Streaming videos or downloading large files can be particularly challenging.
Why is Tor Slow?
- Multiple Hops: Each hop through the Tor network adds latency.
- Encryption Overhead: Encrypting and decrypting data at each node takes time.
- Limited Bandwidth: The Tor network relies on volunteer-operated servers, which may have limited bandwidth.
- Congestion: High traffic on the Tor network can lead to congestion and slower speeds.
Who Uses Tor and Why?
Tor is used by a diverse range of individuals and organizations for various purposes:
- Journalists and Whistleblowers: Tor provides a secure channel for journalists to communicate with sources and protect sensitive information.
- Activists and Human Rights Defenders: Tor helps activists bypass censorship and communicate securely in repressive regimes.
- Privacy-Conscious Individuals: Many people use Tor to protect their online privacy from surveillance and tracking.
- Law Enforcement and Intelligence Agencies: Ironically, Tor is also used by law enforcement and intelligence agencies for covert operations and online investigations.
- Everyday Users: Some people use Tor to access websites that are blocked in their region or to protect their privacy when using public Wi-Fi.
The Exit Node Vulnerability
While Tor provides strong anonymity, the exit node is a potential vulnerability. The exit node decrypts the final layer of encryption, meaning it can potentially see the traffic passing through it. This is why using HTTPS is crucial. An attacker operating an exit node could potentially intercept unencrypted data, such as login credentials or sensitive information. It's important to remember that while Tor hides your IP address, it doesn't guarantee complete security.
The Future of Tor
The Tor Project continues to develop and improve the Tor network, addressing security vulnerabilities and enhancing performance. Ongoing research focuses on developing more efficient routing algorithms, improving encryption techniques, and expanding the network's capacity. As online privacy concerns grow, Tor is likely to remain a vital tool for protecting anonymity and freedom of expression.
Conclusion
Tor is a powerful tool for enhancing your online privacy and anonymity. By understanding how it works and following best practices, you can significantly reduce your digital footprint and protect yourself from surveillance and tracking. However, it's important to remember that Tor is not a silver bullet. It's crucial to use it responsibly and in conjunction with other security measures to maximize your online safety.
Staying Safe: Using Tor and VPNs for Enhanced Privacy
Tor, or The Onion Router, is a powerful tool designed to protect your online privacy. However, using Tor alone isn't always enough to guarantee complete anonymity. There are several ways your identity could still be revealed, and understanding these vulnerabilities is crucial for staying safe online.
Understanding Tor's Limitations
Simply using the Tor browser doesn't automatically make you invisible. Here's a breakdown of the potential risks:
- ISP Detection: Your Internet Service Provider (ISP) can see that you're connecting to the Tor network. While they might not know exactly what you're doing, the fact that you're using Tor can raise red flags. This can lead to your activity being flagged as suspicious, potentially attracting unwanted attention.
- Malicious Exit Nodes: Tor uses a network of volunteer-operated servers, called nodes, to route your traffic. The final node, the exit node, is where your traffic leaves the Tor network and enters the open internet. If a malicious actor operates this exit node, they could potentially intercept your data. This is especially risky if you're visiting websites that don't use HTTPS encryption.
- Website Blocking: Some websites actively block traffic from known Tor IP addresses. This can make it difficult to access certain online resources.
- Browser Fingerprinting: Even with Tor, websites can still collect information about your browser, such as your screen resolution, installed plugins, and fonts. This information can be combined to create a unique "fingerprint" that can be used to track you across different websites.
- Human Error: Often, the weakest link in any security system is the user. Accidentally revealing personal information, such as logging into a personal email account while using Tor, can compromise your anonymity.
The Power of Combining Tor with a VPN
To address these vulnerabilities, using a Virtual Private Network (VPN) in conjunction with Tor (Tor over VPN) is highly recommended. A VPN encrypts your internet traffic before it even reaches the Tor network. This adds an extra layer of security and makes it much harder for your ISP or other third parties to track your online activity.
How Tor over VPN Works
When you use Tor over VPN, your traffic first travels through an encrypted tunnel to the VPN server. From there, it enters the Tor network. This means that your ISP can only see that you're connecting to the VPN server, not that you're using Tor. This effectively masks your Tor usage and provides an additional layer of privacy.
Practical Advice for Tor and VPN Usage
- Choose a Reputable VPN: Not all VPNs are created equal. Look for a VPN provider with a strong privacy policy, a no-logs policy, and a proven track record of security. Research VPN reviews and comparisons to find a provider that meets your needs.
- Use HTTPS Everywhere: Make sure you're visiting websites that use HTTPS encryption. This will protect your data from being intercepted by malicious exit nodes or other third parties.
- Disable Browser Plugins: Browser plugins like Flash and Java can reveal your real IP address. Disable them or use a browser that doesn't support them.
- Avoid Logging into Personal Accounts: Don't log into personal email, social media, or other accounts while using Tor. This can compromise your anonymity.
- Use a Dedicated Tor Browser: Don't use your regular browser for Tor. Use the official Tor Browser, which is specifically designed for privacy and security.
- Update Your Software: Keep your Tor Browser and VPN software up to date. Software updates often include security patches that can protect you from vulnerabilities.
- Consider a Tails Operating System: For extremely sensitive activities, consider using the Tails (The Amnesic Incognito Live System) operating system. Tails is designed to be booted from a USB drive or DVD and leaves no trace on the computer's hard drive. It routes all internet traffic through Tor and includes a suite of privacy-focused tools.
- Understand the Risks of JavaScript: JavaScript can be used to gather information about your browser and potentially reveal your identity. Consider disabling JavaScript in the Tor Browser's security settings, but be aware that this can break some websites.
- Use a Strong Password Manager: Create strong, unique passwords for all your online accounts and use a password manager to store them securely.
- Be Mindful of File Downloads: Avoid downloading files while using Tor, as they can reveal your real IP address. If you must download files, do so after disconnecting from Tor and using a VPN.
- Use Bridged Tor Connections: If Tor is blocked in your region, use bridges. Bridges are obfuscated Tor relays that make it harder for censors to detect and block Tor traffic.
- Regularly Clear Browser Data: Clear your browser history, cookies, and cache regularly to minimize the amount of information that websites can collect about you.
- Practice OpSec (Operational Security): Think carefully about the information you share online. Minimize the amount of personal information you reveal and be aware of the potential risks of sharing sensitive data.
Why People Use Tor
Tor was originally developed for military purposes, but it has since become a valuable tool for a wide range of users. Here are some of the key reasons why people use Tor:
Protecting Privacy
Many people use Tor simply to protect their online privacy. They want to browse the internet without being tracked by advertisers, websites, or their ISP. Tor helps to mask their IP address and encrypt their traffic, making it harder to link their online activity to their real identity.
Avoiding Surveillance
In countries with strict surveillance laws, Tor can be a lifeline for individuals who want to communicate and access information without being monitored by the government. Tor allows them to bypass censorship and access blocked websites.
Accessing Restricted Content
Some websites and online services are only available in certain countries. Tor can be used to bypass these geographic restrictions and access content that would otherwise be unavailable.
Journalists and Activists
As mentioned earlier, Tor is an essential tool for journalists and activists who work in environments where their safety and freedom of expression are at risk. Tor allows them to communicate with sources, share information, and access blocked websites without fear of persecution.
Whistleblowers
Whistleblowers often use Tor to anonymously disclose confidential information to journalists or other organizations. This allows them to expose wrongdoing without risking their identity or facing retaliation.
Law Enforcement
Law enforcement agencies sometimes use Tor to conduct undercover investigations and gather intelligence on criminal activities.
Individuals in Oppressive Regimes
In countries with oppressive governments, Tor provides a critical tool for citizens to access uncensored news and information, communicate with the outside world, and organize dissent.
Beyond the Basics: Advanced Tor Usage
For those requiring extreme levels of security, there are more advanced techniques. Using a live operating system like Tails, as previously mentioned, is one. Also, using a dedicated hardware router with Tor preconfigured can add security. Furthermore, using PGP encryption for emails and messages further protects the user.
Understanding the layers of security offered by Tor and VPNs, and knowing how to configure them properly, is essential for maintaining online privacy and safety. Remember that no tool can guarantee complete anonymity, but by following best practices and staying informed, you can significantly reduce your risk.
Understanding Tor: Privacy, Anonymity, and Its Complexities
Tor, often referred to as "The Onion Router," is a powerful tool designed to enhance online privacy and anonymity. While it's frequently associated with activists and journalists, its applications extend far beyond these circles. Everyday internet users are increasingly turning to Tor to reclaim control over their digital footprint.
Why Ordinary Users Choose Tor
Imagine browsing the internet without being constantly tracked by advertisers. Or accessing content that's blocked in your region. This is where Tor shines. Many people use Tor to:
- Avoid Targeted Advertising: Companies collect vast amounts of data about your online activities to serve personalized ads. Tor disrupts this tracking, preventing advertisers from building detailed profiles of your browsing habits.
- Prevent Tracking by Companies: Websites and online services often use cookies and other tracking technologies to monitor your behavior. Tor masks your IP address and encrypts your traffic, making it harder for companies to track you across different websites.
- Bypass Geographical Restrictions: Streaming services like Netflix, social media platforms, and even search engines often restrict content based on your location. Tor allows you to appear as if you're browsing from a different country, unlocking content that would otherwise be unavailable. For example, if you're traveling and want to access your home country's streaming library, Tor can help.
- Access Blocked Content: In countries with strict internet censorship, Tor provides a lifeline to access news, social media, and other websites that are blocked by the government. This is crucial for individuals seeking information and freedom of expression.
- Protect Privacy in Restrictive Environments: Whether it's a workplace or a school with overly restrictive internet policies, Tor can help you access websites and services that are blocked on the network.
Practical Advice: When using Tor for everyday browsing, consider installing the Tor Browser on a dedicated device or virtual machine. This helps separate your Tor activities from your regular browsing, further enhancing your privacy. Also, be mindful of the websites you visit while using Tor. Stick to HTTPS websites whenever possible, as this ensures that your connection to the website is encrypted.
The Role of Tor in Whistleblowing
Tor has played a pivotal role in enabling whistleblowers to expose wrongdoing without revealing their identities. One of the most prominent examples is Edward Snowden, who used Tor and other encrypted tools to leak classified documents about mass surveillance programs. His actions highlighted the importance of anonymity in protecting individuals who expose government and corporate misconduct.
Whistleblowers often face significant risks, including job loss, legal repercussions, and even physical harm. Tor provides a layer of anonymity that allows them to share sensitive information with journalists and other trusted parties without being easily traced. This is crucial for exposing corruption, human rights abuses, and other illegal activities.
Example: Imagine an employee working for a company that's involved in illegal environmental dumping. They want to report this activity to the authorities but fear retaliation from their employer. By using Tor, they can anonymously contact journalists or regulatory agencies and provide them with evidence of the company's wrongdoing.
Insight: The use of Tor by whistleblowers underscores the importance of anonymity in a democratic society. It allows individuals to hold powerful institutions accountable and expose wrongdoing without fear of reprisal.
The Dark Side: Tor and Illegal Activities
While Tor offers numerous legitimate benefits, its anonymity also attracts individuals who engage in illegal activities. The same features that protect whistleblowers and activists can be exploited by cybercriminals, hackers, and operators of illicit online marketplaces.
Some of the illegal activities that are often associated with Tor include:
- Cybercrime: Hackers use Tor to conceal their identities while launching cyberattacks, distributing malware, and stealing sensitive data.
- Illegal Marketplaces: Darknet marketplaces, which operate on the Tor network, are used to buy and sell illegal goods and services, such as drugs, weapons, and stolen data.
- Child Exploitation: Unfortunately, Tor is sometimes used to distribute and access child sexual abuse material.
- Hacking and Data Breaches: Hackers may use tor to hide their IP addresses while attempting to access secured networks and steal data.
Detailed Discussion: The existence of these illegal activities raises complex ethical and legal questions about Tor. While the tool is essential for protecting privacy and enabling freedom of expression, it also poses challenges for law enforcement agencies. Balancing these competing interests is a difficult task.
Practical Advice: It's crucial to understand that using Tor for illegal activities is not only unethical but also carries significant risks. Law enforcement agencies are increasingly sophisticated in their ability to track down individuals who engage in illegal activities on the Tor network. Moreover, participating in illegal activities on any network, including Tor, can lead to severe legal consequences.
Understanding Tor's Limitations
It's important to understand that Tor is not a silver bullet for online anonymity. While it significantly enhances privacy, it's not foolproof. Some of the limitations of Tor include:
- Exit Node Vulnerabilities: The exit node, which is the last relay in the Tor network, can potentially see unencrypted traffic if you're visiting a website that doesn't use HTTPS.
- Correlation Attacks: Sophisticated adversaries may be able to correlate traffic patterns and deanonymize Tor users.
- Malicious Tor Relays: Some Tor relays may be operated by malicious actors who are trying to monitor or manipulate traffic.
- Browser Fingerprinting: Even with Tor, websites can still collect information about your browser and operating system, which can be used to identify you.
- Human Error: Mistakes like revealing personal information while using Tor can compromise your anonymity.
Practical Advice: To mitigate these risks, use Tor in conjunction with other privacy-enhancing tools and practices. For example, use a strong VPN in conjunction with tor, use a privacy-focused operating system, disable JavaScript whenever possible, and avoid revealing personal information while using Tor.
The Future of Tor
Tor remains a vital tool for privacy-conscious individuals, activists, and whistleblowers. As online surveillance becomes increasingly pervasive, the need for tools like Tor will only grow. Developers are constantly working to improve Tor's security and usability, and new features are being added to address emerging threats.
The ongoing debate about Tor's role in society highlights the tension between privacy and security. Finding a balance between these competing interests is crucial for ensuring that the internet remains a space for freedom of expression and innovation.
In conclusion, Tor is a powerful tool with a complex history and a wide range of applications. While it offers significant benefits for privacy and anonymity, it's essential to understand its limitations and use it responsibly. By educating ourselves about Tor and its complexities, we can make informed decisions about how to protect our privacy in the digital age.
Cybercrime and the Dark Web: A Deeper Dive
The Tor network, often called the Onion Router, is a tool designed to provide online anonymity. While it has legitimate uses, it's also become synonymous with the dark web and the criminal activities that thrive there. Let's break down how this works and what it means for everyday internet users.
Understanding the Dark Web
Imagine the internet as an iceberg. The surface web, accessible through Google, Bing, and other search engines, is just the tip. Below the surface lies the deep web, which includes content not indexed by standard search engines, like your online banking portal or private cloud storage. Deeper still is the dark web, a small portion of the deep web accessible only through specific software, like the Tor browser.
The dark web is known for its anonymity. This anonymity is achieved by routing internet traffic through multiple layers of encryption and relays, making it extremely difficult to trace the origin of a connection. This feature, while valuable for privacy, makes it attractive to criminals.
Illegal Marketplaces and the Silk Road
One of the most infamous examples of dark web activity is the Silk Road. This online marketplace, accessible only through Tor, facilitated the sale of illegal drugs, weapons, and other illicit goods. Although law enforcement shut it down, its legacy lives on. Similar marketplaces continue to emerge, highlighting the ongoing challenge of policing the dark web.
These marketplaces often use cryptocurrencies like Bitcoin for transactions, adding another layer of anonymity. While cryptocurrency transactions are recorded on a public ledger, tracing the real-world identities of the individuals involved can be complex and time-consuming.
Practical Advice: Avoid interacting with dark web marketplaces. The risks of scams, malware, and law enforcement involvement are incredibly high. Even browsing these sites can expose you to harmful content and potentially compromise your security.
Cybercriminals and Their Activities
Beyond marketplaces, the dark web is a haven for cybercriminals. Hackers use Tor to conduct various illegal activities, including:
- Identity Theft: Stealing personal information to commit fraud.
- Fraud: Conducting financial scams and other deceptive practices.
- Cyberattacks: Launching malware, ransomware, and DDoS attacks.
- Data Leaks: Selling or leaking stolen data from companies and individuals.
Ransomware groups often use Tor to communicate with victims, demand payments, and leak stolen data if their demands are not met. The anonymity provided by Tor makes it difficult for law enforcement to track these groups and recover stolen funds.
Practical Advice: Protect yourself from cybercrime by using strong passwords, enabling two-factor authentication, and keeping your software up to date. Be cautious of suspicious emails and links, and never share sensitive information online.
Hosting Hidden Services (Onion Services)
Tor not only allows users to browse anonymously but also to host websites anonymously. These hidden services, known as onion services, can only be accessed through the Tor network. This feature is used for both legitimate and illegal purposes.
Legitimate Uses of Onion Services
Onion services can provide secure communication platforms for journalists, activists, and whistleblowers who need to protect their identities. They can also be used to bypass censorship in countries with restrictive internet policies.
For example, news organizations might host secure drop boxes on the Tor network, allowing sources to anonymously submit sensitive information. Social media platforms might offer onion services to provide users in censored regions with access to their services.
Illegal Uses of Onion Services
Unfortunately, onion services are also used to host dark web marketplaces, forums for cybercriminals, and extremist propaganda sites. The anonymity provided by Tor makes it difficult to shut down these sites and prosecute their operators.
These sites can spread harmful content, including child pornography, hate speech, and instructions for illegal activities. They can also be used to coordinate cyberattacks and other criminal operations.
Practical Advice: Be aware of the risks associated with browsing onion services. Many sites contain illegal and harmful content. Exercise caution and avoid interacting with sites that appear suspicious or illegal.
Is Tor Legal? An In-Depth Analysis
The legality of using Tor is a complex issue. In most Western countries, using Tor itself is legal. However, using Tor to engage in illegal activities is not. It's crucial to understand this distinction.
Think of it like a car. Owning and driving a car is legal, but using it to commit a crime, like robbing a bank, is not. Similarly, using Tor for legitimate purposes, like protecting your privacy, is legal. But using it to buy drugs or engage in other illegal activities is not.
Law enforcement agencies recognize the legitimate uses of Tor, but they are also aware of its potential for misuse. They often monitor the dark web for illegal activities and work to identify and prosecute criminals who use Tor.
Key Legal Considerations:
- Jurisdiction: Laws regarding Tor usage can vary by country. Some countries may have restrictions or bans on Tor usage.
- Intention: The legality of Tor usage depends on the user's intent. Using Tor to protect privacy is generally legal, while using it to commit crimes is not.
- Evidence: Law enforcement agencies can use various techniques to identify and prosecute criminals who use Tor, even though it provides anonymity.
Practical Advice: Use Tor responsibly and avoid engaging in any illegal activities. If you're unsure about the legality of a particular activity, consult with a legal professional.
Balancing Privacy and Security
Tor highlights the ongoing tension between privacy and security in the digital age. While privacy is essential for protecting individuals from surveillance and censorship, it can also be exploited by criminals.
Governments and law enforcement agencies are constantly working to balance these competing interests. They are developing new technologies and strategies to combat cybercrime while respecting individuals' privacy rights.
Key Considerations:
- Encryption: Encryption is a powerful tool for protecting privacy, but it can also be used by criminals to hide their activities.
- Anonymity: Anonymity can protect individuals from surveillance, but it can also be used to facilitate illegal activities.
- Surveillance: Surveillance can be used to prevent and investigate crime, but it can also be used to violate individuals' privacy rights.
Practical Advice: Be mindful of your online activities and take steps to protect your privacy. Use strong passwords, enable two-factor authentication, and be cautious of sharing personal information online. Support policies that balance privacy and security.
Conclusion
Tor is a powerful tool with both positive and negative implications. While it provides valuable privacy protections for journalists, activists, and privacy-conscious individuals, it also facilitates illegal activities on the dark web. The key is responsible use and a clear understanding of the legal and ethical considerations involved.
The digital landscape is constantly evolving, and the challenges of balancing privacy and security will continue to be a central focus. By staying informed and taking proactive steps to protect ourselves, we can navigate this complex environment safely and responsibly.
Understanding Tor: Privacy, Security, and Its Limitations
Tor, often hailed as a bastion of online privacy, is a powerful tool. However, it's crucial to understand that it's not a magic bullet. Many people believe that simply using Tor grants them complete anonymity, but that's a dangerous misconception. Like any technology, Tor has its limitations and vulnerabilities.
The Myth of Absolute Anonymity
The core concept of Tor is to route your internet traffic through multiple volunteer-operated servers, making it difficult for anyone to trace the origin of your connection. This multi-layered approach, known as onion routing, effectively obscures your IP address and online activity. However, this doesn't guarantee absolute anonymity.
Think of it like this: imagine sending a letter through a series of intermediaries, each opening and resealing the envelope. While each intermediary only knows the previous and next step, they don't know the original sender or the final recipient. If a compromised intermediary exists, it can compromise the whole process. Similarly, if the first or last server in the Tor circuit is compromised, your activity can be exposed.
Browser Vulnerabilities: A Common Weak Point
Tor developers are transparent about the fact that vulnerabilities often arise at the browser level, not within the core Tor network itself. This means that even if the Tor network itself is secure, flaws in the browser you use can expose your identity.
For example, browser plugins, JavaScript, and other active content can leak information about your system, such as your operating system, browser version, and even your real IP address. This is why the Tor Browser is specifically designed with security and privacy in mind, disabling many features that could compromise your anonymity.
Practical advice: Always use the official Tor Browser Bundle, which is pre-configured for maximum security. Avoid installing additional plugins or extensions, as they can introduce vulnerabilities. Keep your Tor Browser updated to the latest version, as updates often include security patches.
Traffic Analysis: Monitoring Tor Users
Even with Tor's robust encryption, internet service providers (ISPs) and law enforcement agencies can still employ traffic analysis techniques to identify Tor users. While these methods don't necessarily reveal your specific activities, they can indicate that you're using Tor.
Here's how it works: ISPs can monitor the timing and size of your network traffic. By correlating this data with traffic patterns on Tor entry and exit nodes, they can infer that you're using Tor. This is akin to observing a crowd entering a building with a specific entrance and exit, even if you can't see what they're doing inside.
Law enforcement agencies might use this information to monitor individuals suspected of illegal activities. While simply using Tor is not illegal in most countries, it can raise red flags and attract attention, especially if your activity involves accessing the dark web.
Example: If a large number of connections are made from a specific IP address to known Tor entry nodes, this can be flagged as suspicious activity. Authorities might then monitor these connections for further investigation. This is not breaking the tor encryption, but simply observing the use.
Compromised Exit Nodes: A Potential Threat
Exit nodes are the final servers in the Tor circuit, where your traffic leaves the Tor network and enters the regular internet. If a malicious actor controls an exit node, they can intercept unencrypted traffic, such as HTTP websites or email without SSL/TLS. This means they could potentially see your login credentials, personal information, or other sensitive data.
Practical advice: Always use HTTPS websites, which encrypt your traffic even after it leaves the Tor network. Use a VPN in conjunction with Tor for an added layer of security, especially if you're concerned about exit node compromise. Ensure your operating system and applications are updated to patch security vulnerabilities. Consider using onion services (websites ending in .onion) whenever possible, as they keep your traffic within the Tor network, avoiding exit nodes altogether.
Human Error: The Biggest Vulnerability
Often, the biggest vulnerability in any security system is human error. Even with the most sophisticated technology, mistakes like revealing personal information, clicking on malicious links, or downloading infected files can compromise your anonymity.
Example: If you log into your personal email account or social media profile while using Tor, your real identity can be linked to your Tor activity. Similarly, if you download a file containing malware, it could reveal your IP address or other identifying information.
Practical advice: Be extremely cautious about the information you share online while using Tor. Avoid logging into personal accounts, and be wary of downloading files or clicking on links from untrusted sources. Use strong, unique passwords for all your online accounts, and enable two-factor authentication whenever possible. Practice good digital hygiene and be aware of phishing scams and social engineering tactics.
Metadata Leaks: Unintended Information Disclosure
Metadata, which is data about data, can reveal a surprising amount of information about your online activity. Even if your content is encrypted, metadata such as file sizes, timestamps, and communication patterns can be used to infer your identity or activities.
Example: If you send a large file through Tor, the size of the file itself can be used to infer the type of content, such as a video or audio file. Similarly, the timing of your communications can reveal patterns that identify you or your associates.
Practical advice: Be mindful of the metadata you generate. Avoid sending large files or using services that generate excessive metadata. Use tools that strip metadata from files before sharing them. Consider using encrypted messaging apps that minimize metadata collection.
Tor and Law Enforcement: A Complex Relationship
While Tor is often associated with illegal activities, it's important to remember that it's a valuable tool for journalists, activists, and individuals living under oppressive regimes. Law enforcement agencies also use Tor for undercover investigations and to protect the anonymity of their sources.
However, the use of Tor can attract law enforcement attention, especially if your activity is deemed suspicious. Authorities may employ various techniques to monitor Tor users, including traffic analysis, exit node monitoring, and even infiltrating Tor networks.
It is important to understand that law enforcement agencies have the resources and capabilities to investigate online activities. They can obtain warrants to compel ISPs to provide information about their subscribers, and they can work with international partners to track online activity across borders.
Practical advice: Use Tor responsibly and ethically. Avoid engaging in illegal activities while using Tor. Be aware that your online activity can be monitored, even with Tor. Consider using additional security measures, such as a VPN, if you're concerned about law enforcement surveillance.
Conclusion: Tor as a Tool, Not a Shield
Tor is a powerful tool for enhancing online privacy, but it's not a foolproof solution. It's crucial to understand its limitations and to use it responsibly. By being aware of the potential vulnerabilities and taking appropriate precautions, you can maximize your privacy and security while using Tor.
Remember, Tor is a tool, not a shield. It's one piece of a larger puzzle that includes good digital hygiene, strong passwords, encrypted communications, and a healthy dose of skepticism. By combining these practices, you can significantly enhance your online privacy and security.
Privacy vs. Security: Understanding the Difference and Staying Safe Online
Many people believe that having more privacy automatically means they're more secure online. However, that's not always the case. Privacy and security, while related, are distinct concepts. Think of it like this: privacy is about keeping your information hidden, while security is about protecting it from harm. You can have a locked diary (security), but someone might still know you have one (lack of privacy). Conversely, you can hide your diary in a secret place (privacy), but it might not be locked (lack of security).
Tor: Enhanced Privacy, Not Guaranteed Security
The Tor browser is a great example of this distinction. It's designed to provide strong privacy by routing your internet traffic through multiple servers, making it difficult to trace your online activity. This network encryption is indeed very robust, making it tough for anyone to intercept your data and see where you're going online. Additionally, Tor's open-source nature is a huge plus. Because anyone can examine the code, security vulnerabilities are often discovered and fixed quickly by a community of developers and researchers. This transparency helps keep the network strong.
However, while Tor excels at privacy, it doesn't automatically guarantee security. The Tor browser itself, like any software, can have vulnerabilities. It's still susceptible to cyberattacks, malware, and sophisticated tracking techniques. For example, if you download a malicious file while using Tor, your computer could become infected, regardless of the privacy provided by the network.
Understanding Man-in-the-Middle (MITM) Attacks
One significant risk users face, even with Tor, is the Man-in-the-Middle (MITM) attack. In this type of attack, someone intercepts the communication between you and the website you're visiting. This could be your internet service provider (ISP), a hacker, or even a malicious actor operating a rogue Tor relay. They can see or even modify the data being transmitted. While Tor's encryption makes it difficult for them to decipher the content, they might still be able to see that you're using Tor and potentially track your activity to some extent.
Imagine you're sending a letter through a network of post offices (like Tor). The letter is sealed (encrypted), but someone working at one of the post offices might still be able to see that you sent a letter and where it's going, even if they can't read what's inside. This is a simplified analogy of how a MITM attack can compromise your privacy, even when using Tor.
Practical Advice for Enhancing Security While Using Tor
To maximize your security while using Tor, consider these practical tips:
- Keep Tor Updated: Regularly update your Tor browser to the latest version. Updates often include patches for newly discovered vulnerabilities, making it harder for attackers to exploit them.
- Update Your Operating System: Ensure your operating system (Windows, macOS, Linux, etc.) is also up to date. Security updates for your OS often fix vulnerabilities that could be exploited by malware or other attacks.
- Use a Reliable Antivirus and Anti-Malware: Install and regularly update a reputable antivirus and anti-malware program. This can help protect your computer from malicious software that could compromise your security, regardless of whether you're using Tor.
- Be Cautious About Downloading Files: Avoid downloading files from untrusted sources, even while using Tor. Malicious files can infect your computer and compromise your security.
- Use HTTPS: Always make sure the websites you visit use HTTPS. This encrypts the communication between your browser and the website, making it harder for attackers to intercept your data. Look for the padlock icon in your browser's address bar.
- Disable JavaScript: While JavaScript can enhance website functionality, it can also be used for tracking and other malicious purposes. Consider disabling JavaScript in your Tor browser's security settings, especially when visiting sensitive websites. However, be aware that some websites may not function properly without JavaScript.
- Use Bridges or Pluggable Transports: If Tor is blocked in your region, use bridges or pluggable transports. These techniques can help you connect to the Tor network even if it's being blocked.
- Avoid Using Personal Information: Don't use your real name, email address, or other personal information while using Tor. This can help protect your anonymity.
- Use a VPN with Tor (Carefully): Using a Virtual Private Network (VPN) in conjunction with Tor can add an extra layer of security. However, it's crucial to choose a reputable VPN provider that doesn't keep logs of your activity. Using a VPN before Tor can provide a higher level of anonymity. Using a VPN after Tor may be less secure due to the exit node being able to see your unencrypted traffic.
- Be Aware of Exit Nodes: Tor exit nodes are the final servers in the Tor network that relay your traffic to the destination website. These nodes can see your traffic if it's not encrypted (HTTPS). Be cautious about entering sensitive information on websites that don't use HTTPS.
- Use Tails OS: Tails (The Amnesic Incognito Live System) is an operating system designed for privacy and anonymity. It routes all traffic through Tor and leaves no trace on the computer after use. This can be a more secure option than using Tor on a regular operating system.
- Educate Yourself: Stay informed about the latest security threats and best practices. Follow reputable security blogs and websites to learn about new vulnerabilities and how to protect yourself.
The Importance of Layered Security
Think of security as an onion with multiple layers. Each layer provides a different level of protection. Relying on a single layer, like Tor, isn't enough. You need to combine different security measures to create a robust defense against online threats. This includes using strong passwords, enabling two-factor authentication, being cautious about clicking on links or opening attachments, and regularly backing up your data.
Beyond Technical Measures: Understanding Social Engineering
Technical security measures are essential, but they can be bypassed through social engineering. Social engineering involves manipulating people into revealing confidential information or performing actions that compromise their security. This can include phishing emails, fake websites, or even phone calls from scammers. Be wary of unsolicited requests for personal information, and always verify the identity of anyone asking for sensitive data.
The Evolving Landscape of Online Security
The online security landscape is constantly evolving. New threats and vulnerabilities are discovered every day. Staying informed and adapting your security practices is crucial to protecting yourself in this ever-changing environment. Consider taking online security courses or attending workshops to enhance your knowledge and skills.
Conclusion: A Balanced Approach to Privacy and Security
In conclusion, while Tor provides enhanced privacy, it doesn't guarantee security. It's essential to understand the distinction between these two concepts and adopt a balanced approach. By combining strong technical measures with careful online behavior, you can significantly reduce your risk of becoming a victim of cybercrime. Remember, security is an ongoing process, not a one-time fix. Stay vigilant, stay informed, and stay safe.
--- ### **Should You Use Tor?** For an average internet user, the anonymity provided by Tor may not be compelling enough to justify its use. One major drawback is that Tor significantly **slows down internet speed** due to its encryption process and multi-layered routing. Additionally, governments and intelligence agencies focus their surveillance efforts on suspicious online activities rather than mass surveillance of all users. If your primary online activities involve streaming videos, searching for nearby restaurants, or casual browsing, Tor may not offer any substantial benefit. However, Tor is useful for individuals facing **internet censorship, journalists working in authoritarian regimes, whistleblowers, and privacy-conscious users**. If these concerns apply to you, Tor can be a valuable tool.VPN vs. Tor: Which is Right for You?
Navigating the digital world safely can feel like a minefield. You've probably heard of Tor and VPNs, both touted as tools for online privacy and security. But which one is the better choice? Or, perhaps, do you need both?
Let's break it down in simple terms.
Understanding Tor: The Anonymity Network
Tor, short for "The Onion Router," is designed to anonymize your internet traffic. Imagine your data wrapped in layers, like an onion. Each layer gets peeled away as it passes through different servers (called nodes) on the Tor network. This makes it incredibly difficult for anyone to trace your activity back to you.
Key Strengths of Tor:
- High Anonymity: Tor excels at hiding your IP address and location.
- Access to the Dark Web: It's the primary gateway to the dark web, a part of the internet not indexed by standard search engines.
- Free to Use: Tor is open-source and free, relying on volunteer-run servers.
Limitations of Tor:
- Slow Speeds: The multiple layers of encryption and routing slow down your internet connection significantly. Streaming or downloading large files can be frustrating.
- Limited Protection: Tor primarily protects your browser traffic. Applications outside the Tor browser, like your email client or file-sharing software, remain vulnerable.
- Potential Risks: While Tor enhances anonymity, it doesn't guarantee complete security. Some exit nodes (the final servers your traffic passes through) might be compromised. Also, using Tor for illegal activities can attract unwanted attention.
- User Interface and Usability: Tor can be less intuitive for non-technical users.
Practical Advice for Using Tor:
- Use the Tor Browser Only: Stick to the Tor browser for all activities requiring anonymity. Avoid opening other applications while using Tor.
- Disable Plugins: JavaScript and other plugins can reveal your real IP address. Disable them in the Tor browser settings.
- Avoid Downloading Files: Downloading files through Tor can expose your IP address.
- Be Mindful of Exit Nodes: Understand that exit nodes can see your unencrypted traffic if you are visiting a non https website.
Understanding VPN: The Security Shield
A Virtual Private Network (VPN) creates an encrypted tunnel between your device and a remote server. This hides your IP address and encrypts your internet traffic, protecting it from prying eyes.
Key Strengths of a VPN:
- Comprehensive Encryption: A VPN encrypts all your internet traffic, regardless of the application you're using.
- Fast Speeds: VPNs generally offer much faster speeds than Tor, enabling smooth streaming and downloading.
- Geo-Restriction Bypass: VPNs allow you to change your virtual location, accessing content restricted to specific regions.
- Ease of Use: VPNs are user-friendly, with simple interfaces and one-click connections.
- Protection on Public Wi-Fi: VPNs secure your connection on public Wi-Fi networks, preventing hackers from intercepting your data.
- Protection Against ISP Tracking: VPNs prevent your Internet Service Provider (ISP) from tracking your browsing history.
Limitations of a VPN:
- Centralized Control: Your privacy depends on the VPN provider's trustworthiness. Choose a reputable provider with a strong no-logs policy.
- Subscription Fees: Most reliable VPNs require a subscription fee.
- Limited Anonymity: While VPNs hide your IP address, they don't offer the same level of anonymity as Tor.
- No Dark Web Access: VPNs don't provide direct access to the dark web.
Practical Advice for Choosing and Using a VPN:
- Choose a Reputable Provider: Research VPN providers and read reviews. Look for providers with a strong no-logs policy, meaning they don't track your online activity.
- Consider Server Locations: Choose a VPN with servers in locations relevant to your needs.
- Check Encryption Protocols: Ensure the VPN uses strong encryption protocols like OpenVPN or WireGuard.
- Use a Kill Switch: A kill switch automatically disconnects your internet connection if the VPN connection drops, preventing your real IP address from being exposed.
- Avoid Free VPNs: Free VPNs often have limited features, slower speeds, and may even collect your data.
Tor vs. VPN: A Detailed Comparison
Security:
- Tor: Offers strong anonymity but limited security. Vulnerable to exit node attacks and applications outside the Tor browser.
- VPN: Provides comprehensive security by encrypting all traffic. Relies on the provider's trustworthiness.
Speed:
- Tor: Significantly slower due to multiple layers of encryption and routing.
- VPN: Much faster, enabling smooth streaming and downloading.
Usability:
- Tor: Can be complex for non-technical users.
- VPN: User-friendly with simple interfaces.
Anonymity:
- Tor: Offers high anonymity by hiding your IP address and routing traffic through multiple servers.
- VPN: Hides your IP address but doesn't offer the same level of anonymity as Tor.
Access to the Dark Web:
- Tor: Provides access to the dark web.
- VPN: Doesn't provide direct access to the dark web.
Combining Tor and VPN: Enhanced Privacy and Security
For maximum privacy and security, you can use Tor and a VPN together. There are two ways to do this:
- Tor over VPN: Connect to a VPN first, then launch the Tor browser. This hides your VPN connection from your ISP and adds an extra layer of encryption.
- VPN over Tor: Connect to Tor first, then launch your VPN. This hides your real IP address from the VPN provider, but can be more complex to set up.
Using Tor with a VPN can protect you from potential malware, phishing, and hacking attempts often associated with the dark web. It also provides an extra layer of protection against surveillance and tracking.
When to Use Tor and When to Use a VPN
Use Tor when:
- You need high anonymity, such as for whistleblowing or political activism.
- You need to access the dark web.
- You want to bypass censorship in highly restrictive environments.
Use a VPN when:
- You want to protect your privacy on public Wi-Fi.
- You want to bypass geo-restrictions and access region-locked content.
- You want to encrypt all your internet traffic for enhanced security.
- You want to prevent your ISP from tracking your browsing history.
- You want faster speeds for streaming and downloading.
Conclusion
Tor and VPNs are valuable tools for online privacy and security. The best choice depends on your specific needs and priorities. If you need high anonymity and access to the dark web, Tor is essential. If you want comprehensive security, faster speeds, and ease of use, a VPN is a better option. For maximum protection, consider using both Tor and a VPN together.
Navigating Online Privacy: Tor vs. VPN - Making the Right Choice
In today's digital age, online privacy is no longer a luxury, but a necessity. With increasing surveillance, data breaches, and targeted advertising, understanding the tools available to protect your digital footprint is crucial. Two prominent options often discussed are Tor and VPNs. But which one is right for you?
Understanding Tor
Tor, or The Onion Router, is a free, open-source software that anonymizes your internet traffic by routing it through multiple volunteer-operated servers, or "nodes." This layered encryption, resembling the layers of an onion, makes it difficult to trace your online activity back to you.
Key Features and Benefits
- Anonymity: Tor excels at concealing your IP address and online activity, providing a high level of anonymity. This is particularly useful for journalists, activists, and individuals in countries with strict censorship.
- Access to the Dark Web: Tor allows access to hidden services on the dark web, which can be useful for accessing information not readily available on the surface web.
- Circumventing Censorship: Tor can bypass internet censorship and firewalls, allowing access to blocked websites and services.
Limitations and Drawbacks
- Slow Speed: The multi-layered encryption process significantly slows down internet speeds, making Tor unsuitable for bandwidth-intensive activities like streaming or gaming.
- Potential Security Risks: While Tor provides anonymity, it's not foolproof. Exit nodes, the last server in the Tor network, can potentially monitor traffic. Additionally, Tor has been known to be targeted by malicious actors and government agencies.
- Complexity: While Tor is user-friendly, understanding its intricacies and configuring it correctly can be challenging for some users.
- Not suitable for all activities: Tor is not ideal for activities where speed is paramount, or where real time interactions are required.
- Legal Concerns: In some regions, simply using Tor can raise suspicion from authorities, even if you're not engaging in illegal activities.
- Vulnerability to Correlation Attacks: If an attacker can monitor both your entry and exit points, they might be able to correlate the data and de-anonymize your traffic.
Practical Advice for Tor Users
- Use HTTPS: Always ensure websites use HTTPS encryption to protect your data between the exit node and the website.
- Disable Scripts: Disable JavaScript in your Tor browser settings to prevent potential vulnerabilities.
- Avoid Downloading Files: Downloading files through Tor can expose your IP address.
- Use a Bridge: If Tor is blocked in your region, use a bridge to connect to the network.
- Keep Tor Updated: Regularly update your Tor browser to patch security vulnerabilities.
- Don't use personal information: avoid logging into personal email or social media accounts while using Tor.
- Use a dedicated OS: Consider using Tails (The Amnesic Incognito Live System), a live operating system designed for privacy and anonymity.
Understanding VPNs
A Virtual Private Network (VPN) creates an encrypted tunnel between your device and a remote server, masking your IP address and encrypting your internet traffic. This provides a layer of security and privacy, but it differs significantly from Tor.
Key Features and Benefits
- Enhanced Security: VPNs encrypt your internet traffic, protecting it from eavesdropping and data breaches.
- Faster Speeds: Compared to Tor, VPNs offer significantly faster speeds, making them suitable for streaming, gaming, and downloading.
- Access to Geo-restricted Content: VPNs allow you to bypass geo-restrictions and access content from different regions.
- Ease of Use: VPNs are generally easy to set up and use, with user-friendly interfaces.
- Protection on Public Wi-Fi: VPNs secure your connection on public Wi-Fi networks, protecting your data from potential threats.
- Consistent Performance: VPNs offer more consistent performance than Tor, which can experience fluctuating speeds.
Limitations and Drawbacks
- Centralized Trust: VPNs rely on a centralized server, meaning your privacy is dependent on the VPN provider's policies and practices.
- Potential Logging: Some VPN providers may log user activity, compromising your privacy. Always choose a reputable VPN with a strict no-logs policy.
- Cost: While there are free VPNs, they often have limitations and may compromise your privacy. Paid VPNs offer better performance and security.
- Not Perfect Anonymity: While VPNs hide your IP address, they don't provide the same level of anonymity as Tor.
Practical Advice for VPN Users
- Choose a Reputable Provider: Research and choose a VPN provider with a proven track record of security and privacy.
- Check the Logging Policy: Ensure the VPN provider has a strict no-logs policy.
- Use Strong Encryption: Choose a VPN that uses strong encryption protocols like OpenVPN or WireGuard.
- Enable the Kill Switch: Use a VPN with a kill switch feature, which automatically disconnects your internet connection if the VPN connection drops.
- Use a Secure Server: Choose a server in a country with strong privacy laws.
- Regularly update: Keep your vpn software updated.
- Check for IP and DNS Leaks: Use online tools to verify that your VPN is not leaking your IP address or DNS requests.
Tor vs. VPN: Which One to Choose?
The choice between Tor and a VPN depends on your specific needs and priorities:
- For Maximum Anonymity: If your primary goal is to achieve maximum anonymity, especially for activities like whistleblowing or accessing censored content, Tor may be the better choice.
- For Everyday Privacy and Security: If you prioritize everyday privacy and security, along with faster speeds and ease of use, a reputable VPN is a more practical option.
- For Streaming and Gaming: If you need high-speed internet for streaming, gaming, or downloading large files, a VPN is the clear winner.
- For Accessing Geo-restricted Content: A VPN is the best choice for bypassing geo-restrictions and accessing content from different regions.
- For protecting data on public wifi: A VPN is the best choice for this.
Combining Tor and VPN
For enhanced security and anonymity, you can combine Tor and a VPN. Using a VPN before connecting to Tor (VPN-over-Tor) adds an extra layer of encryption and masks your IP address from your ISP and the Tor entry node. However, this configuration can further slow down your internet speed.
Staying Informed and Safe
Regardless of whether you choose Tor, a VPN, or both, staying informed about cybersecurity risks is crucial. Keep your software updated, use strong passwords, and be cautious about the information you share online. Remember, no tool can provide absolute security or anonymity. Your online safety ultimately depends on your own vigilance and responsible online behavior.
Understanding the strengths and weaknesses of each tool will help you make an informed decision and take control of your online privacy.
Understanding Tor and Proxy Servers: A Simple Guide
When we talk about online privacy and security, you'll often hear terms like "Tor" and "proxy servers." They both aim to mask your online identity, but they work very differently. It's like comparing a bicycle to a bus – both get you from point A to B, but their methods, speed, and capacity vary greatly.
What is a Proxy Server?
Imagine a post office. When you send a letter, you write your return address. With a proxy server, it's like sending your letter through a middleman. The middleman (the proxy server) puts its own return address on the letter before forwarding it. So, to the recipient, the letter seems to come from the middleman, not you.
In the digital world, a proxy server acts as an intermediary between your computer and the internet. When you visit a website, your request goes to the proxy server first. The proxy server then forwards the request to the website on your behalf. The website sees the proxy server's IP address, not yours.
Types of Proxy Servers
- HTTP Proxies: These are designed for web traffic. They handle requests for web pages.
- SOCKS Proxies: These are more versatile and can handle various types of internet traffic, including email and file transfers.
- Transparent Proxies: These proxies don't hide your IP address; they're often used for content filtering or caching.
- Anonymous Proxies: These attempt to hide your IP address, but they might not be completely secure.
- High Anonymity Proxies (Elite Proxies): These are the most secure type of proxy, as they don't reveal that you're using a proxy server.
Practical Uses of Proxy Servers
- Bypassing Geo-restrictions: Accessing content that's blocked in your region. For example, watching a streaming service that's only available in another country.
- Accessing Blocked Websites: Getting around workplace or school firewalls.
- Caching: Storing frequently accessed web pages to speed up loading times.
- Content Filtering: Blocking access to certain websites or types of content, often used by businesses or schools.
Limitations of Proxy Servers
- Security Risks: Many free proxies are unreliable and may log your activity or inject malware. Paid proxies can be more secure, but they still don't offer the same level of security as Tor or a VPN.
- Lack of Encryption: Most proxies don't encrypt your traffic, meaning your data can be intercepted and read by third parties.
- Performance Issues: Free proxies are often slow and overloaded, leading to poor performance.
- Single Point of Failure: If the proxy server is compromised, your data is at risk.
What is Tor?
Tor, or The Onion Router, is a network designed for anonymity. It's like sending your letter through a series of multiple middlemen, each of whom only knows the previous and next middleman in the chain. Each layer of the "onion" represents a different server, and each layer encrypts your data. By the time the data reaches its destination, it's been encrypted and routed through multiple servers, making it very difficult to trace back to you.
How Tor Works
- Onion Routing: Your data is encrypted in layers and sent through a network of volunteer-operated servers (nodes).
- Multiple Hops: Your traffic passes through at least three nodes: the entry node, the middle node(s), and the exit node.
- Dynamic Routing: The path your traffic takes through the Tor network changes frequently, making it harder to track.
Practical Uses of Tor
- Anonymity: Protecting your identity and online activity from surveillance.
- Bypassing Censorship: Accessing blocked websites and services in countries with strict internet censorship.
- Whistleblowing: Securely leaking sensitive information without revealing your identity.
- Journalism: Protecting the identity of sources and journalists in high-risk environments.
Limitations of Tor
- Slow Speed: The multiple layers of encryption and routing can significantly slow down your internet connection.
- Exit Node Vulnerability: The exit node, where your traffic leaves the Tor network, can see your unencrypted data if you're not using HTTPS.
- Not Foolproof: Tor can be compromised by advanced adversaries, especially if you make mistakes like revealing personal information while using it.
- Blocked by Some Services: Some websites and services block Tor users due to concerns about abuse.
Tor vs. Proxy Servers: Key Differences
| Feature | Tor | Proxy Server |
|---|---|---|
| Anonymity | High | Variable (Low to Moderate) |
| Security | High (Multiple layers of encryption) | Variable (Often lacks encryption) |
| Speed | Slow | Variable (Can be fast or slow) |
| Routing | Multiple hops through volunteer servers | Single hop through a single server |
| Use Cases | Anonymity, censorship circumvention, whistleblowing | Bypassing geo-restrictions, accessing blocked websites, caching |
| Reliability | Relatively reliable, but can be slow | Variable, often unreliable |
| Encryption | Strong encryption | Often no encryption |
Practical Advice and Insights
When to Use a Proxy Server
If you need to quickly bypass a geo-restriction or access a blocked website and don't require strong anonymity, a proxy server might be sufficient. However, be cautious about using free proxies, as they can pose security risks. If you use a proxy, consider a reputable paid service, and always use HTTPS when possible.
When to Use Tor
Use Tor when you need strong anonymity and security, such as when accessing sensitive information, communicating with sources in high-risk environments, or bypassing strict censorship. Remember that Tor is not a silver bullet. Practice good security habits, such as avoiding logging into personal accounts while using Tor and using HTTPS whenever possible. Consider using a VPN in conjunction with Tor for added security. (VPN -> Tor is recommended)
Additional Security Tips
- Use a VPN: A Virtual Private Network (VPN) encrypts your internet traffic and hides your IP address, adding an extra layer of security.
- Keep Software Updated: Regularly update your operating system, browser, and other software to patch security vulnerabilities.
- Use Strong Passwords: Use unique, complex passwords for your online accounts, and consider using a password manager.
- Enable Two-Factor Authentication (2FA): Add an extra layer of security to your accounts by requiring a second form of verification, such as a code from your phone.
- Be Careful What You Click: Avoid clicking on suspicious links or downloading files from untrusted sources.
- Use HTTPS: Always use HTTPS when browsing websites, as it encrypts your connection.
- Limit Personal Information: Don't share sensitive personal information online unless absolutely necessary.
- Review Privacy Settings: Regularly review and adjust the privacy settings on your online accounts.
Understanding the Risks
Both proxies and Tor have limitations. No online tool can guarantee complete anonymity. Understanding the risks associated with each tool is crucial for making informed decisions about your online security and privacy. Always weigh the benefits against the potential risks, and use these tools responsibly.
The Importance of Layered Security
Think of online security like building a fortress. One wall alone might not be enough to keep intruders out. That's why layered security is essential. Combining different security measures, such as a VPN, Tor, and strong passwords, can create a robust defense against online threats. By understanding the strengths and weaknesses of each tool, you can create a security strategy that meets your specific needs.
In conclusion, while proxy servers and Tor both serve to hide your IP address, they are vastly different in their functionality and security levels. Understanding these differences is essential for making informed choices about your online privacy and security.
Understanding Proxy Servers: Your Internet Intermediary
Imagine you're sending a letter to a friend in another country. Instead of sending it directly, you give it to a middleman who then forwards it. This middleman is like a proxy server for your internet traffic.
In simple terms, a proxy server sits between your computer or device and the websites or online services you want to reach. When you type a website address into your browser, your request doesn't go straight to that website. Instead, it goes to the proxy server first. The proxy server then forwards your request to the website, and when the website sends back its response, the proxy server delivers it to you.
Why Use a Proxy Server?
There are several reasons why people use proxy servers. Let's break down the most common ones:
1. Masking Your IP Address (Basic Anonymity)
Every device connected to the internet has a unique IP address, like a digital home address. When you use a proxy, your real IP address is hidden, and the website sees the IP address of the proxy server instead. This can give you a degree of anonymity. For example, if you're browsing from India and using a proxy server located in the US, the website will think you're browsing from the US.
Practical Advice: While this offers some anonymity, remember that a simple proxy alone doesn't guarantee complete privacy. Anyone who controls the proxy server can still see your real IP and your browsing activity.
2. Bypassing Content Restrictions
Some websites or services are blocked in certain countries or regions. For instance, a streaming service might only be available in specific locations. A proxy server can help you bypass these restrictions by making it appear as if you're browsing from a permitted location.
Example: If a YouTube video is blocked in your country, you could use a proxy server in a country where it's available to watch it.
Practical Advice: Be aware that using proxies to bypass restrictions might violate the terms of service of certain websites. It's essential to understand the legal and ethical implications before doing so.
3. Improving Performance (Caching)
Some proxy servers can cache frequently accessed web pages. This means they store copies of these pages. When you or someone else requests a cached page, the proxy server can deliver it directly, which is much faster than fetching it from the original website. This can improve browsing speed and reduce bandwidth usage.
Insight: Caching is particularly useful in environments with limited bandwidth or high network traffic, such as corporate networks or educational institutions.
4. Controlling Internet Usage (Filtering)
In organizations like schools or workplaces, proxy servers can be used to filter and control internet access. Administrators can block access to certain websites or content, ensuring that users comply with policies and guidelines.
Example: A school might use a proxy server to block access to social media websites during school hours.
Practical Advice: If you're using a proxy server provided by your organization, be aware that your internet activity might be monitored and logged.
Types of Proxy Servers
Not all proxy servers are created equal. Here's a breakdown of the different types:
1. HTTP Proxies
These proxies are specifically designed for web traffic (HTTP and HTTPS). They're commonly used for browsing websites and are relatively easy to set up.
2. SOCKS Proxies
SOCKS proxies are more versatile and can handle any type of internet traffic, including email, FTP, and peer-to-peer file sharing. They offer a higher degree of flexibility compared to HTTP proxies.
3. Transparent Proxies
These proxies operate without the user's knowledge. They are often used by ISPs or organizations to control and monitor internet traffic. They don't offer anonymity as they don't hide your IP address.
4. Anonymous Proxies
These proxies hide your IP address, making it appear as if you're browsing from a different location. They provide a basic level of anonymity.
5. High Anonymity (Elite) Proxies
These proxies not only hide your IP address but also prevent websites from detecting that you're using a proxy. They offer the highest level of anonymity among proxy servers.
6. Reverse Proxies
Unlike forward proxies, which sit between the user and the internet, reverse proxies sit in front of web servers. They are used to protect web servers from direct internet traffic, improve performance, and provide load balancing.
Limitations and Security Considerations
While proxy servers offer various benefits, they also have limitations and security risks:
1. Lack of Encryption
Many free or public proxy servers don't encrypt your internet traffic. This means that your data can be intercepted and viewed by anyone on the network, including the proxy server operator.
Practical Advice: If you're handling sensitive information, such as passwords or financial data, avoid using unencrypted proxy servers. Always ensure that the website you're visiting uses HTTPS.
2. Logging and Monitoring
Proxy server operators can log your IP address, browsing history, and other data. This information can be used for various purposes, including targeted advertising or even malicious activities.
Insight: Free proxy services often monetize their operations by selling user data to third parties. Be cautious when using such services.
3. Performance Issues
Free or overloaded proxy servers can be slow and unreliable, leading to a poor browsing experience. They might also inject ads or other unwanted content into web pages.
4. Security Risks
Some proxy servers might be compromised or operated by malicious actors. They could inject malware into your downloads or redirect you to phishing websites.
Practical Advice: Choose reputable proxy server providers and avoid using free or unknown services. Look for providers with strong security measures and transparent privacy policies.
5. Shared IP Vulnerability
As mentioned, everyone using a proxy shares the same IP. If someone using the same proxy performs malicious actions, the proxy's IP could be blacklisted, affecting all users.
When to Use a Proxy Server
Here are some scenarios where using a proxy server might be beneficial:
- Bypassing geo-restrictions: Accessing content that's blocked in your region.
- Basic anonymity: Hiding your IP address for casual browsing.
- Improving performance: Caching frequently accessed web pages.
- Controlling internet usage: Filtering content in organizations.
- Testing websites: Viewing how a website appears from different locations.
Alternatives to Proxy Servers
For stronger privacy and security, consider these alternatives:
1. Virtual Private Networks (VPNs)
VPNs encrypt your internet traffic and hide your IP address, providing a higher level of security and privacy compared to proxy servers. They are generally more reliable and offer a wider range of features.
2. Tor Browser
The Tor Browser routes your traffic through multiple layers of encryption, making it extremely difficult to trace your online activity. It's ideal for those seeking maximum anonymity.
3. Secure DNS Services
Services like Cloudflare DNS or Google Public DNS can improve your online privacy and security by encrypting your DNS queries and protecting you from malicious websites.
Conclusion
Proxy servers can be useful tools for various purposes, from basic anonymity to bypassing content restrictions. However, it's crucial to understand their limitations and security risks. Choose reputable providers, use them responsibly, and consider alternatives like VPNs or Tor for stronger privacy and security. By taking these precautions, you can make informed decisions about using proxy servers and protect your online presence.
Understanding Online Privacy: Why Tor and VPNs Outshine Proxies
In today's digital age, safeguarding your online privacy is more crucial than ever. While proxies, Tor, and VPNs all offer ways to mask your IP address, they differ significantly in their security and reliability. Many people opt for proxies due to their perceived ease of use and often free nature. However, it's essential to understand that "free" doesn't always equate to "secure." Let's delve into why Tor and VPNs provide superior protection.
The Shortcomings of Proxies
Proxies act as intermediaries between your device and the internet, masking your IP address. However, their security limitations are substantial:
-
Lack of Encryption:
The most significant drawback of proxies is their lack of data encryption. While they hide your IP, your internet traffic remains vulnerable to interception. This means anyone monitoring the network, such as your internet service provider (ISP) or a malicious actor, can potentially view your data. Practical Advice: If you're using a public Wi-Fi network, avoid accessing sensitive information like banking details or personal emails through a proxy alone.
-
Trust and Reliability Issues:
The security of a proxy is entirely dependent on the trustworthiness of the server's operator. Many free proxies are run by unknown entities, making it impossible to verify their security practices. Some may log your activity, inject ads, or even sell your data. Example: Imagine using a free proxy to browse online banking. The proxy operator could potentially log your login credentials and access your account. Practical Advice: Be wary of free proxies. If you must use one, research the provider and understand their logging policies.
-
Data Logging Risks:
Proxy servers have full access to your traffic, creating a significant risk of data logging. This can include your browsing history, personal information, and even sensitive data like passwords. Insight: Some proxy operators may legally be required to log data, depending on their jurisdiction.
-
Security Threats:
Proxies often lack robust security measures, making them susceptible to man-in-the-middle attacks. In these attacks, a hacker intercepts your communication with a website, potentially stealing or manipulating your data. Example: A hacker could intercept your login credentials when you access a website through a vulnerable proxy. Practical Advice: Avoid using proxies for activities involving sensitive data, especially on public Wi-Fi.
The Superior Security of Tor and VPNs
Tor and VPNs address the shortcomings of proxies by providing robust encryption and enhanced security features.
-
Encryption:
Both Tor and VPNs encrypt your internet traffic, making it significantly harder for anyone to intercept and read your data. VPNs typically encrypt all traffic from your device, while Tor encrypts traffic through multiple layers of relays. Insight: VPNs are ideal for everyday browsing and streaming, while Tor is better suited for highly sensitive activities.
-
Trust and Reliability:
Reputable VPN providers like Private Internet Access (PIA), ExpressVPN, and NordVPN invest heavily in security and transparency. They have clear privacy policies and are accountable for their actions. Tor, being a decentralized network, relies on volunteer-run relays, enhancing its anonymity. Practical Advice: Choose a VPN provider with a strong reputation, a no-logs policy, and transparent ownership.
-
Data Logging Risks
Reputable VPN services have strict “no-logs” policies, meaning they do not store records of your online activity. Tor, by its nature, is designed to minimize data logging. Insight: Always review the privacy policy of any VPN or service you use.
-
Security Threats
VPNs and Tor employ advanced security protocols to protect against various threats, including man-in-the-middle attacks. They also often include features like kill switches and DNS leak protection. Practical Advice: Enable the kill switch feature in your VPN to prevent data leaks if the connection drops.
Installing Tor Browser: A Step-by-Step Guide
Tor Browser is a modified version of Firefox that routes your internet traffic through the Tor network, providing enhanced anonymity. Here's how to install it:
Step 1: Download Tor Browser
Visit the official Tor Project website at https://www.torproject.org. Click the "Download" button.
Step 2: Choose Your Operating System
Select the appropriate version for your operating system (Windows, macOS, Linux, or Android). For specific language versions, click "Download in another language or platform."
Step 3: Run the Installer
Locate the downloaded file and run it:
- Windows: Double-click the .exe file.
- macOS: Open the .dmg file.
- Linux: Extract the tar.xz package and follow the instructions.
- Android: Download from the Google Play Store or install the .apk file (ensure it's from the official Tor Project site).
Step 4: Complete the Installation
The installation wizard will guide you through the process. Choose your preferred language and installation location. Click "Install."
Step 5: Connect to the Tor Network
After installation, launch Tor Browser. Click "Connect" to automatically connect to the Tor network. If you're in a country where Tor is censored, click "Configure" to set up bridges. Insight: Bridges are Tor relays that are not publicly listed, making them harder to block.
Step 6: Start Browsing Securely
Once connected, you can browse the internet anonymously. However, remember these crucial security tips:
- Avoid logging into personal accounts.
- Don't download or open untrusted files.
- Use HTTPS websites whenever possible.
- Don't install additional browser plugins.
- Keep Tor Browser updated.
Additional Tor Project Tools
The Tor Project offers various tools beyond the Tor Browser:
- Tor Bridges: To bypass censorship.
- OnionShare: To securely share files.
- Tor Snowflake: A pluggable transport to defeat censorship.
Important Security Considerations
While Tor enhances anonymity, it's not foolproof. Be mindful of:
- JavaScript: Disabling JavaScript can enhance security but may break some websites.
- Plugins: Avoid installing browser plugins, as they can compromise your anonymity.
- Website Fingerprinting: Some websites may use advanced techniques to identify you.
- OpSec (Operational Security): Your online behavior can reveal your identity, even when using Tor. Avoid sharing personal information.
By understanding the differences between proxies, Tor, and VPNs, and by following best practices, you can significantly enhance your online privacy and security.
Beyond the Browser: Exploring the Tor Project's Other Tools
Most people know the Tor Project for its famous Tor Browser, a tool designed to help you browse the internet anonymously. However, the Tor Project team is dedicated to more than just anonymous browsing. They've created a suite of tools aimed at protecting your privacy and promoting internet freedom in various ways. Let's delve into some of these projects, understand their purpose, and explore how they contribute to a more private and secure online experience.
Orbot: Your Android Privacy Shield
Imagine having the Tor network's power directly on your Android phone. That's precisely what Orbot offers. It's a free app that acts as a proxy, routing your phone's internet traffic through the Tor network. Just like the Tor Browser, Orbot encrypts your data and sends it through multiple relays, making it incredibly difficult for anyone to track your online activities. This is particularly useful when you're using public Wi-Fi or want to prevent your mobile provider from monitoring your browsing habits.
Practical Advice for Using Orbot:
- Select Apps to Torify: Orbot allows you to choose which apps should use the Tor network. This is crucial because routing all your phone's traffic through Tor can significantly slow down your internet speed. Focus on apps that handle sensitive data, like your email, messaging apps, or your web browser.
- Use a VPN with Orbot: For an extra layer of security, consider using a VPN in conjunction with Orbot. A VPN encrypts your traffic before it enters the Tor network, providing an additional level of anonymity.
- Be Mindful of Battery Consumption: Running Orbot can consume more battery than usual. Adjust your usage accordingly or carry a portable charger.
- Ensure Orbot is Running: Always double-check that Orbot is actively running before using apps that require privacy. A notification icon usually indicates its status.
Insights: Orbot is a powerful tool for mobile privacy. It's especially useful in regions with heavy internet censorship or surveillance. However, it's essential to understand that Orbot only encrypts traffic originating from your phone. If you're accessing websites that use insecure protocols (HTTP instead of HTTPS), your data might still be vulnerable at the destination.
OONI: Shining a Light on Internet Censorship
The Open Observatory of Network Interference (OONI) takes a different approach to internet freedom. Instead of providing tools for anonymity, OONI focuses on documenting and measuring internet censorship worldwide. It's like a global watchdog, monitoring which websites and services are being blocked in different countries.
OONI provides free software that anyone can use to test their internet connection for signs of censorship. When you run an OONI test, it checks if specific websites or services are accessible. The results are then shared with the OONI project, contributing to a global database of internet censorship data.
Key Differences from Tor:
- Focus on Measurement, Not Circumvention: OONI doesn't help you bypass censorship. Instead, it provides evidence of censorship, which can be used by activists, journalists, and researchers to advocate for internet freedom.
- Open Data and Transparency: OONI's data is publicly available, allowing anyone to analyze and understand global censorship trends. This transparency is crucial for holding governments and ISPs accountable.
Practical Applications of OONI Data:
- Journalistic Investigations: Journalists can use OONI data to uncover instances of censorship and report on human rights violations.
- Advocacy and Policy Work: Activists and policymakers can use OONI data to advocate for internet freedom and push for policy changes.
- Research and Analysis: Researchers can use OONI data to study the impact of internet censorship on society and develop strategies for combating it.
Example: Imagine a country where the government blocks access to independent news websites. OONI tests can detect these blocks and provide evidence of censorship. This data can then be used by human rights organizations to raise awareness and pressure the government to lift the restrictions.
Insights: OONI plays a crucial role in promoting internet freedom by providing evidence of censorship. By documenting these restrictions, OONI empowers individuals and organizations to fight for a more open and accessible internet.
Tor Messenger (Discontinued): A Lesson in Security
The Tor Project once developed Tor Messenger, an encrypted chat application designed to provide anonymous communication. It aimed to integrate with popular messaging services like Google Talk, Facebook Messenger, and Twitter, ensuring that your conversations remained private and secure.
Why Was Tor Messenger Discontinued?
The discontinuation of Tor Messenger in 2018 highlights the challenges of maintaining secure communication tools. The ever-evolving threat landscape requires constant updates and maintenance. The Tor Project decided to focus its resources on other projects, recognizing that maintaining a secure messaging application was becoming increasingly difficult.
Lessons Learned:
- Security Requires Constant Vigilance: Maintaining a secure communication tool is an ongoing process that requires continuous updates and monitoring.
- Focus on Core Strengths: The Tor Project's decision to focus on its core strengths, like the Tor Browser and Orbot, demonstrates the importance of prioritizing resources.
- Use Modern Alternatives: With the discontinuation of Tor Messenger, users are advised to use modern, actively maintained encrypted messaging apps like Signal or Matrix.
Insights: The story of Tor Messenger serves as a reminder that security is not a one-time achievement. It requires ongoing effort and adaptation. While the project was discontinued, the lessons learned from its development have contributed to the Tor Project's overall understanding of secure communication.
The Tor Project's Broader Impact
The Tor Project's work extends beyond individual tools. It's a testament to the importance of privacy and freedom in the digital age. By developing and maintaining these tools, the Tor Project empowers individuals to take control of their online experiences and promotes a more open and secure internet for everyone.
The Importance of Privacy:
In an increasingly interconnected world, privacy is more important than ever. Our online activities generate vast amounts of data that can be used to track our movements, monitor our communications, and profile our interests. The Tor Project's tools help to protect this data and ensure that individuals have the right to privacy.
The Fight for Internet Freedom:
Internet censorship and surveillance are growing threats to freedom of expression and access to information. The Tor Project's work helps to combat these threats by providing tools and data that empower individuals and organizations to fight for a more open and accessible internet.
Supporting the Tor Project:
The Tor Project is a non-profit organization that relies on donations and volunteers. You can support their work by donating, volunteering, or simply spreading awareness about their tools and mission.
By understanding and utilizing the tools developed by the Tor Project, we can all contribute to a more private, secure, and free internet.
Understanding Tor: Is It Right for You?
Tor, or The Onion Router, is a tool designed to give you more privacy and anonymity online. It's like a special pathway through the internet that hides your tracks. Imagine sending a letter through a series of intermediaries, each one only knowing where they got it from and where they're sending it next. Tor works similarly, routing your internet traffic through multiple volunteer-operated servers around the world. This makes it much harder for anyone to trace your activity back to you.
People use Tor for many reasons. Some use it to protect their privacy from companies or advertisers that track their online behavior. Others use it to access websites that are blocked in their country, or to communicate securely with sources when they're journalists or activists. It's a powerful tool for those who value their online freedom.
What Tor Does and Doesn't Do
Tor's main strength is its ability to anonymize your web browsing within the Tor Browser. However, it's important to understand its limitations:
- Browser-Specific Protection: Tor only protects the traffic that goes through the Tor Browser. If you use other programs or browsers, they won't have the same level of protection. For example, if you download a file using a regular download manager, it won't be routed through Tor.
- Not a Full Network Encryptor: Unlike a VPN, Tor doesn't encrypt all of your internet traffic. A VPN encrypts everything that leaves your device, while Tor focuses on anonymizing your browsing activity. This means other applications on your device, like email clients or online games, won't have Tor's protection.
- Speed Considerations: Because your traffic is bounced through multiple servers, Tor is generally slower than regular internet browsing. This can be frustrating if you're trying to stream videos or download large files.
- The Dark Web and Its Risks: Tor allows access to the "dark web," a part of the internet not indexed by regular search engines. While it can be a place for legitimate activity, it also has a reputation for hosting illegal content, malware, and scams. Exercise extreme caution when exploring the dark web.
Why Law Enforcement Might Be Watching
Because Tor can be used to hide illegal activities, law enforcement agencies do monitor its usage. They might be looking for patterns or specific individuals. However, simply using Tor doesn't automatically make you a suspect. It's the activities you engage in while using it that matter. If you're using Tor for legitimate privacy reasons, you have nothing to worry about. But if you're using it for illegal purposes, you're taking a significant risk.
Practical Advice for Safe Tor Usage
To maximize your safety and privacy when using Tor, consider these tips:
- Use Tor Browser Only: Stick to using the Tor Browser for all your browsing needs. Don't mix regular browsing with Tor browsing.
- Keep Tor Browser Updated: Regularly update your Tor Browser to ensure you have the latest security patches.
- Disable Browser Plugins: Plugins like Flash or Java can reveal your IP address. Disable them or set them to "click to play."
- Use HTTPS Everywhere: Ensure you're visiting websites that use HTTPS. This encrypts the connection between your browser and the website, making it harder for anyone to eavesdrop.
- Avoid Logging In: Don't log in to personal accounts or websites while using Tor. This can compromise your anonymity.
- Don't Download Torrents: Tor isn't designed for torrenting. Torrenting over Tor can expose your IP address and slow down the network for other users.
- Use a Reputable VPN (With Caution): Combining Tor with a VPN can add an extra layer of security. However, it's crucial to choose a reputable VPN provider that doesn't keep logs. Placing the VPN before Tor can hide the fact you are using tor from your ISP. Placing the VPN after Tor, known as Tor over VPN, can protect you from malicious exit nodes.
- Use Strong Antivirus and Anti-Malware: Keep your antivirus and anti-malware software updated and running. This will help protect you from malware you might encounter on the dark web or elsewhere.
- Be Wary of Dark Web Links: Only click on links you trust. The dark web can be a breeding ground for scams and malware.
- Don't Reveal Personal Information: Avoid sharing any personal information that could identify you while using Tor.
- Use Tails or Whonix: For even greater security, consider using operating systems like Tails (The Amnesic Incognito Live System) or Whonix. These systems are designed to maximize privacy and anonymity.
- Understanding Exit Nodes: Tor's exit nodes are the last server your traffic passes through before reaching its destination. They can potentially see the traffic if it's not encrypted with HTTPS. Be mindful of this when entering sensitive information.
- Consider Your Threat Model: Think about what you're trying to protect and who you're trying to protect it from. This will help you determine how much security you need.
Tor vs. VPN: Understanding the Differences
Tor and VPNs are often discussed together, but they serve different purposes:
- VPNs: Encrypt all your internet traffic and hide your IP address from websites and your ISP. They're good for general privacy and security, especially on public Wi-Fi.
- Tor: Anonymizes your browsing activity by routing it through multiple servers. It's better for hiding your identity and accessing censored content.
You can use both Tor and a VPN together for enhanced privacy. However, it's essential to understand the implications and risks.
Who Should Use Tor?
Tor is a valuable tool for:
- Journalists and Activists: To protect their sources and communicate securely.
- People Living Under Censorship: To access information and websites that are blocked in their country.
- Privacy-Conscious Individuals: To protect their online privacy from tracking and surveillance.
- Whistleblowers: To anonymously report information.
Who Shouldn't Use Tor?
Tor might not be suitable for:
- People Looking for Fast Browsing: Tor's speed limitations can be frustrating.
- People Who Need Full Network Encryption: Tor only protects browser traffic.
- People Engaging in Illegal Activities: Law enforcement monitors Tor usage.
Conclusion
Tor is a powerful tool for enhancing online privacy and anonymity. However, it's not a silver bullet. Understanding its limitations and taking precautions is crucial for safe and responsible use. By combining Tor with other security measures, you can significantly improve your online privacy and protect yourself from surveillance. Remember to stay informed and vigilant, and always prioritize your online safety.









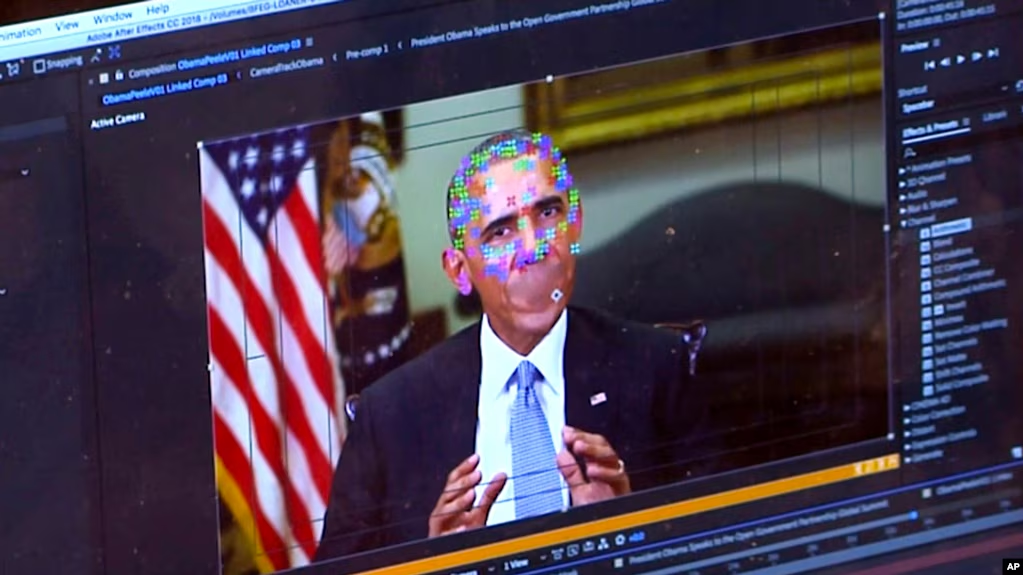


















0 Comments